
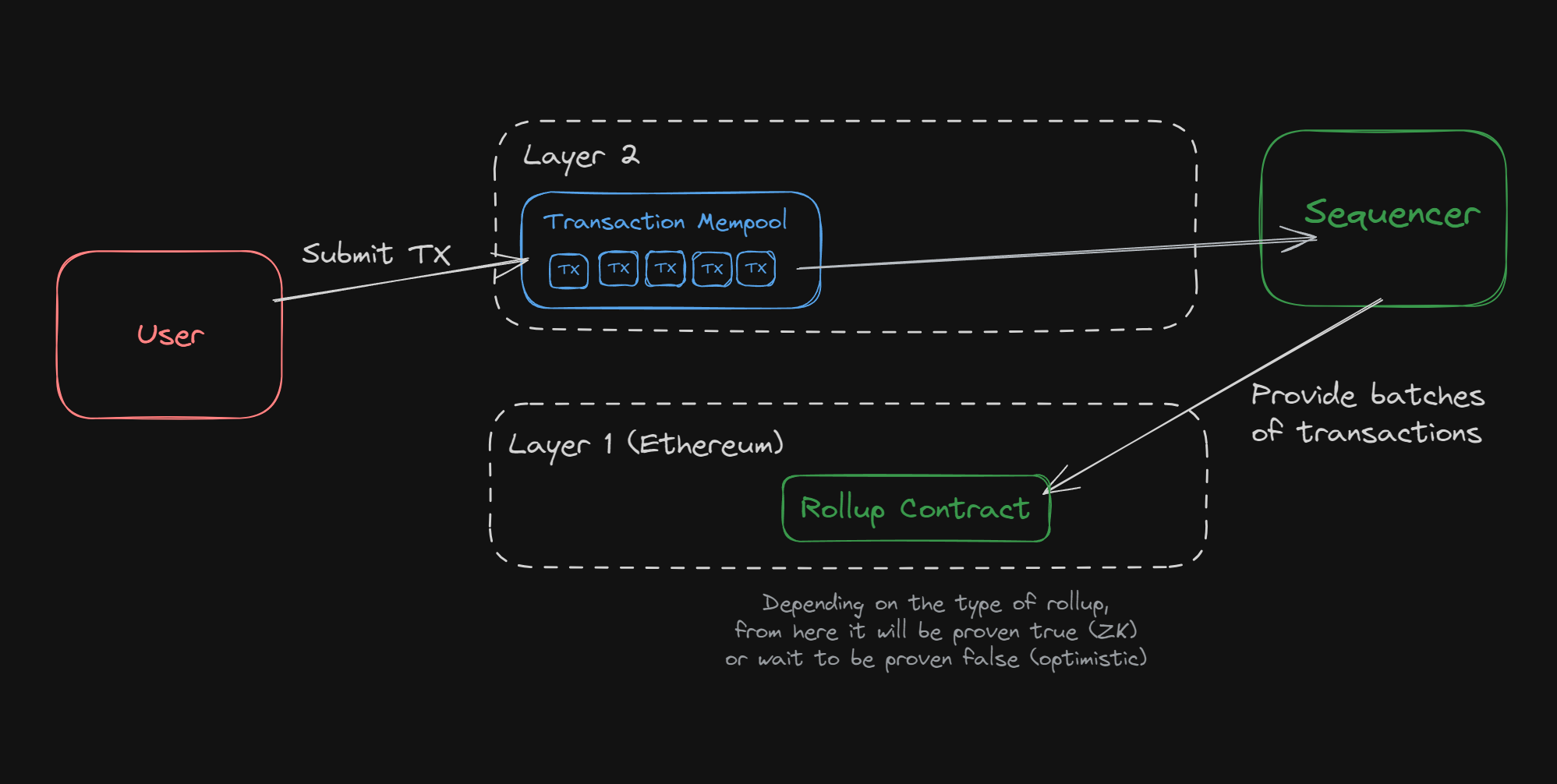
The rapid ascent of Ethereum Layer 2 solutions has revolutionized blockchain scalability, but privacy remains a stubborn challenge. As decentralized applications (dApps) become more sophisticated and handle increasingly sensitive data, the demand for confidential smart contracts is surging. Enter Trusted Execution Environments (TEEs) – specialized secure areas within processors that are redefining what’s possible for encrypted contract protocols on Ethereum Layer 2s.
What Are Trusted Execution Environments and Why Do They Matter?
A Trusted Execution Environment is essentially a secure enclave within a CPU. It allows code and data to be processed in isolation from the rest of the system, shielding them from external observation or tampering. When applied to blockchain infrastructure, TEEs ensure that even node operators cannot access the underlying logic or inputs of confidential smart contracts. This is a game-changer for enterprises and privacy-conscious users seeking robust data protection beyond what zero-knowledge proofs alone can deliver.
Current market leaders like Intel SGX and AMD SEV have made TEEs widely accessible, but their true value emerges when integrated into Layer 2 scaling solutions. By executing smart contract logic inside TEEs, developers can create confidential rollups that combine the throughput advantages of optimistic or ZK rollups with bulletproof privacy guarantees.
The State of Confidential Smart Contracts on Ethereum Layer 2s
The last year has seen an explosion of innovation in this space. Projects like TEN Protocol have built next-generation Layer-2 rollups where encrypted smart contracts operate in shared private states, unlocking use cases such as:
- Private DeFi strategies: Users can deploy trading algorithms without leaking alpha to competitors.
- Confidential DAO voting: Ballots remain secret while outcomes are verifiable on-chain.
- Encrypted messaging dApps: Communication stays private even from infrastructure providers.
Secret Network’s integration with ZKsync Era showcases how decentralized confidential computing layers can be harnessed for private NFTs, encrypted storage, and collaborative AI agents – all secured by Ethereum’s mainnet consensus but executed off-chain inside TEEs. The result is a new paradigm where privacy no longer comes at the expense of speed or composability.
How TEE-Powered Rollups Work: Under the Hood
The core architecture behind TEE-enabled Layer 2s involves running EVM-compatible virtual machines directly inside secure enclaves. For example, research initiatives like RaceTEE have successfully ported Go-Ethereum (Geth) into TEEs to support full-featured contract execution with hardware-enforced confidentiality. This means:
- User inputs and contract state are encrypted end-to-end, visible only within the enclave during execution.
- Transaction logic remains opaque to validators and node operators, eliminating key vectors for front-running or data leakage.
- State updates are committed back to Layer 1 via cryptographic proofs, ensuring trustless settlement without revealing sensitive information.
This architecture enables developers to build truly private dApps on Ethereum without sacrificing interoperability or composability with existing DeFi protocols. The combination of TEE hardware isolation and cryptographic attestation provides a level of assurance unmatched by software-only approaches.
However, integrating TEEs into Ethereum Layer 2s is not without its trade-offs. One of the primary concerns is the reliance on specialized hardware. Since only nodes equipped with TEE-capable processors like Intel SGX or AMD SEV can participate in confidential execution, there is a risk of reduced decentralization. This hardware dependency can also introduce supply chain trust issues, as the security of the entire system ultimately hinges on the integrity of the manufacturer and their firmware updates.
Security researchers have pointed out that while TEEs raise the bar for attackers, they are not invulnerable. Side-channel attacks and exploitation of implementation flaws remain real threats. To mitigate these risks, leading projects are adopting layered security models – combining TEE-based computation with cryptographic techniques such as zero-knowledge proofs or multi-party computation for added robustness.
Despite these challenges, the momentum behind TEE-powered confidential smart contracts continues to build. The introduction of decentralized confidential computing (DeCC) frameworks by networks like Secret Network and their collaboration with major Layer 2 ecosystems is accelerating adoption. Developers now have access to toolkits that make it easier to deploy private dApps for use cases ranging from encrypted NFT metadata to secure data marketplaces and collaborative AI agents.
Strategic Implications for Enterprises and Builders
The emergence of trusted execution environment TEE smart contracts on Ethereum Layer 2s opens new strategic avenues for enterprises seeking regulatory compliance and competitive advantage. Financial institutions can finally build privacy-preserving DeFi products that protect client strategies and comply with data protection mandates such as GDPR or CCPA. Healthcare providers can collaborate on sensitive datasets without exposing patient information on-chain. Even gaming studios can enable play-to-earn economies where player actions and inventories remain confidential.
For builders, the opportunity lies in leveraging encrypted contract protocols to create next-generation private dApps Ethereum users have been demanding. Composability remains intact: confidential contracts can interact seamlessly with public smart contracts, unlocking hybrid workflows where only select information is shielded while maintaining global settlement guarantees.
The Road Ahead: Privacy as a First-Class Primitive
As Ethereum Layer 2 privacy matures, expect a wave of innovation in both protocol design and application development. FHE-Rollups (Fully Homomorphic Encryption Rollups) are already being explored as complementary solutions to TEEs, promising even stronger privacy guarantees at scale. Meanwhile, ongoing research into decentralized attestation could help further reduce trust assumptions around hardware vendors.
The competitive landscape will favor projects that balance performance, usability, and security while making privacy accessible to mainstream users. Ultimately, TEEs are catalyzing a shift where confidentiality is no longer an afterthought but a foundational element of blockchain infrastructure.
The next twelve months will be pivotal as more developers experiment with private dApps powered by TEEs and encrypted contract protocols. For those building at the intersection of scalability and privacy, this is a rare window to shape how trustless systems protect sensitive data in an open world.






