
Confidentiality and composability have long been at odds in public blockchain environments. While the Ethereum Virtual Machine (EVM) has revolutionized programmable money, its transparent nature exposes sensitive data and business logic to competitors, regulators, and adversaries. Enter Fully Homomorphic Encryption (FHE): a cryptographic paradigm that is rapidly transforming how privacy is achieved in decentralized applications by enabling encrypted smart contracts on EVM-compatible chains.
What Is Fully Homomorphic Encryption and Why Does It Matter for Smart Contracts?
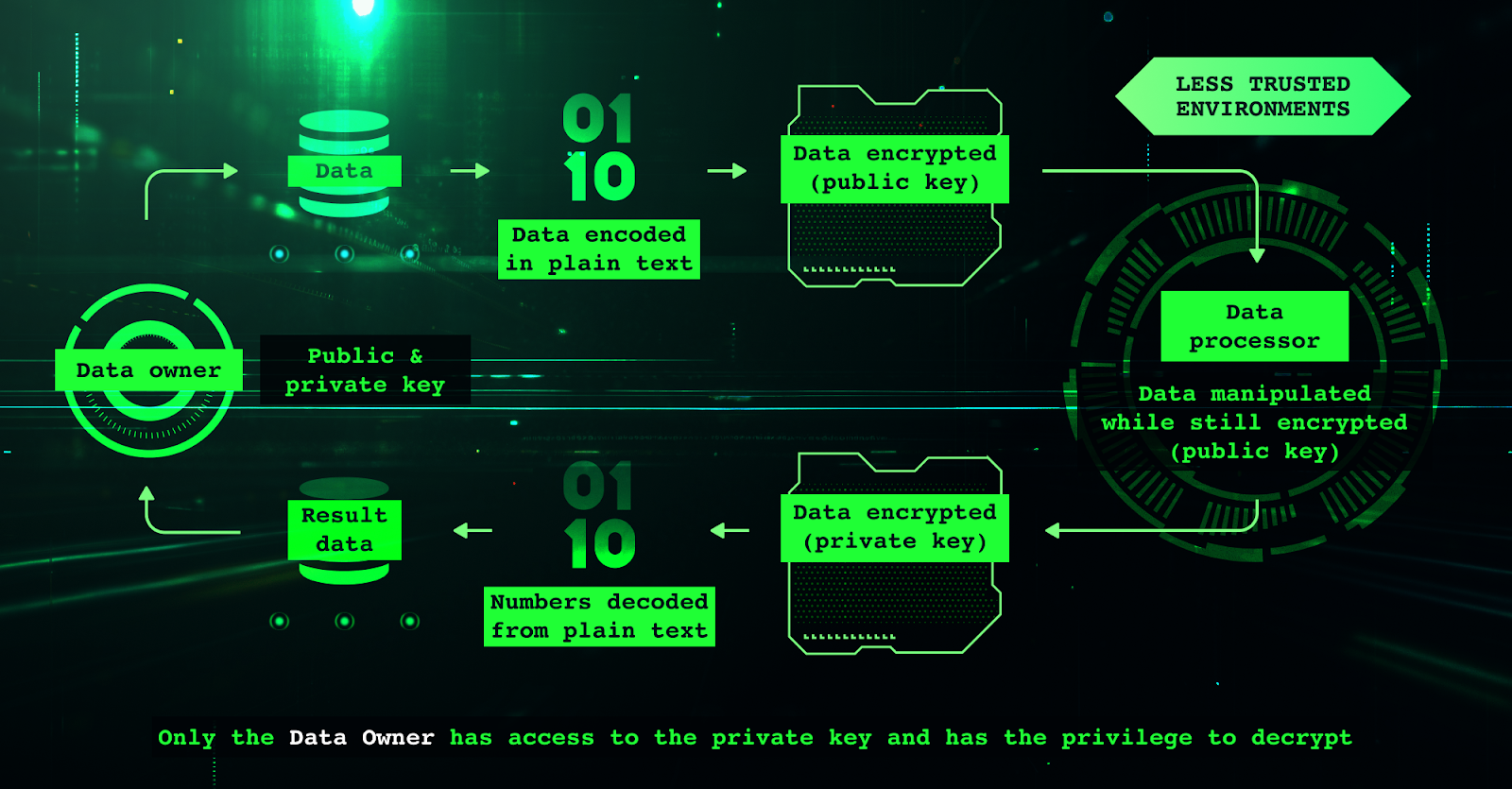
FHE is not just another privacy technology. Unlike zero-knowledge proofs or secure enclaves, FHE allows computations to be performed directly on encrypted data, with no need to ever decrypt inputs or intermediate results during execution. This means that smart contracts can process confidential information, such as financial transactions, user identities, or proprietary algorithms, without ever exposing plaintext data to the blockchain or validators.
The implications are profound: developers can now build private DeFi solutions, on-chain private voting systems, and privacy-preserving AI applications that leverage the security and interoperability of public blockchains without sacrificing confidentiality.
How FHE Is Integrated Into EVM Chains: Key Mechanisms
The push for confidential EVM chains has given rise to several pioneering frameworks. Notably, Zama’s fhEVM extends Solidity with encrypted data types like euint64, euint32, and ebool. These primitives empower developers to perform arithmetic and logic operations on ciphertexts as easily as on standard variables, no advanced cryptography knowledge required.
The actual FHE operations, addition, subtraction, multiplication, are handled by specialized libraries such as TFHE. add, ensuring that all computations remain encrypted throughout their lifecycle. To orchestrate these processes securely:
- Coprocessors: Decentralized services that execute heavy-duty FHE computations off-chain before returning encrypted results to the main chain.
- Gateways: Middleware components responsible for validating encrypted inputs, managing access control lists (ACLs), and coordinating key management protocols.
- MPC-based Key Management: Threshold Multi-Party Computation networks generate and rotate decryption keys so no single party ever holds complete access, critical for trust minimization.
This architecture enables seamless integration of privacy without altering the underlying consensus protocol, a critical factor for scaling confidential smart contracts across existing EVM networks.
Top 5 Benefits of FHE for Confidential Smart Contracts
-

End-to-End Data Privacy: FHE ensures that all sensitive data remains encrypted throughout its entire lifecycle, even during computation. This prevents unauthorized access and exposure of confidential information on public blockchains.
-
Seamless Composability: Confidential smart contracts built with FHE can interact with other contracts and decentralized applications on EVM chains without leaking private data, preserving the interconnected nature of DeFi and Web3 ecosystems.
-

Regulatory Compliance: By keeping data encrypted and confidential, FHE-enabled smart contracts help organizations meet strict data protection regulations, such as GDPR, enabling broader adoption in regulated industries like finance and healthcare.
-

Developer Accessibility: Frameworks like Zama’s fhEVM and Cypher’s FHE-EVM Layer allow developers to build confidential smart contracts in familiar languages like Solidity, without requiring deep cryptographic expertise.
-

Enabling New Use Cases: FHE unlocks innovative applications such as confidential DeFi, private voting, and secure on-chain AI, all while maintaining the transparency and security of blockchain technology.
Pioneering Projects and Real-World Use Cases
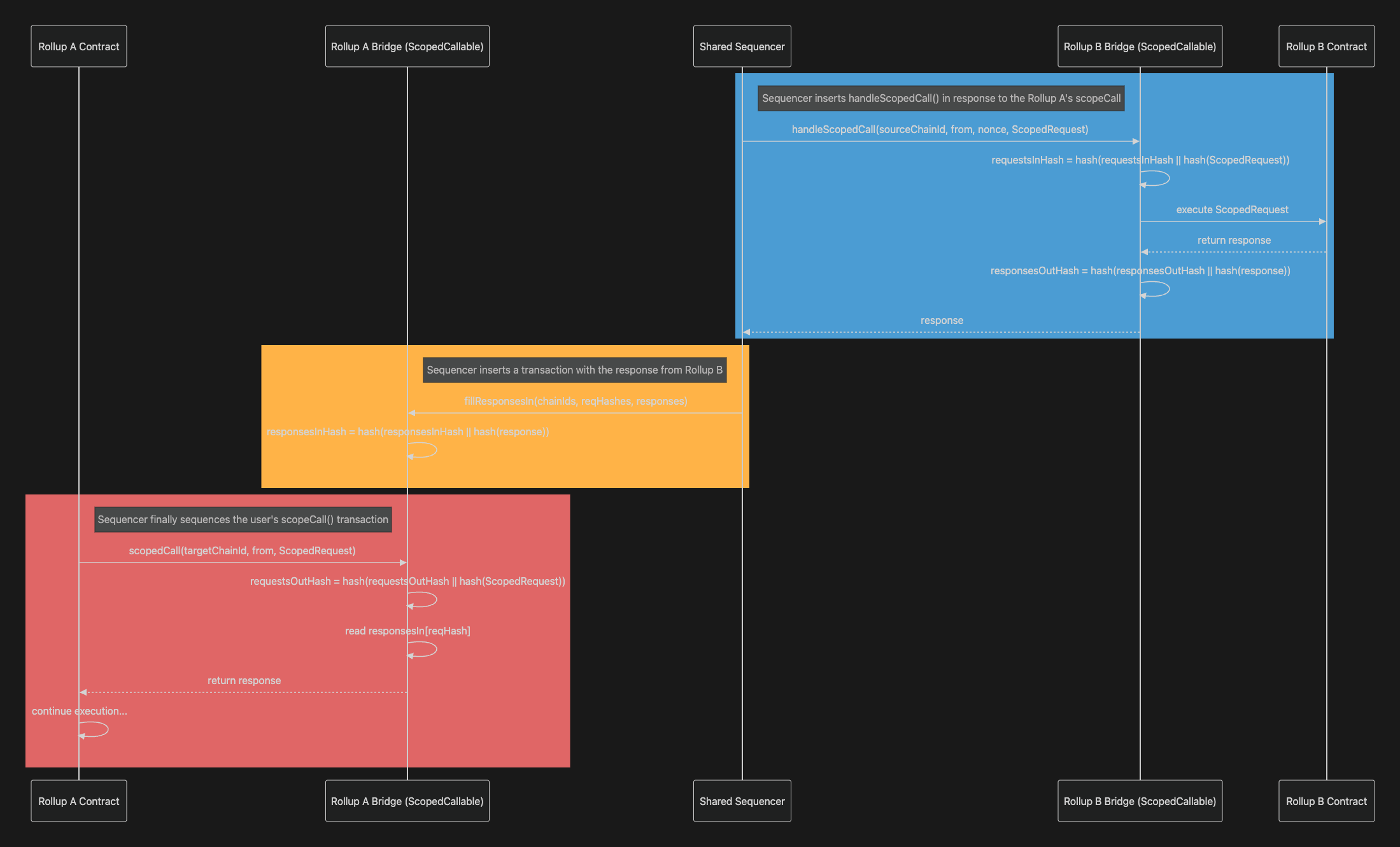
Zama’s fhEVM isn’t the only player in this space. Cypher’s FHE-EVM Layer optimizes encrypted computation for AI-driven dApps while maintaining compatibility with legacy EVM tooling. Meanwhile, projects like Fhenix are lowering the barrier even further by abstracting cryptographic complexity away from developers entirely. This means confidential logic can be deployed on any chain, even those lacking native FHE support, with minimal code changes.
The doors are now open for:
- Private DeFi markets: Encrypted order books where trading strategies remain hidden until settlement.
- On-chain private voting: Anonymous ballots with verifiable outcomes, no trusted tallying authority required.
- Privacy-preserving AI blockchain: Machine learning models that operate over user data without ever seeing it in plaintext, unlocking new forms of secure collaboration between enterprises.
The Road Ahead: From Theory to Scalable Privacy Solutions
The maturation of frameworks like fhEVM signals a paradigm shift for blockchain privacy. By integrating fully homomorphic encryption directly into the heart of EVM-compatible chains, and leveraging decentralized coprocessors alongside robust MPC key management, the industry is moving beyond proof-of-concept toward real-world deployment at scale. As regulatory pressure mounts around data protection, these advances are set to become not just desirable but essential infrastructure for next-generation decentralized applications.
However, the journey from cryptographic theory to seamless, developer-friendly privacy tooling is ongoing. The current generation of FHE-enabled confidential smart contracts offers a promising foundation, but practical deployment is not without hurdles. Performance remains a central challenge: even with optimized coprocessors and off-chain computation, FHE operations are still more resource-intensive than their plaintext counterparts. The trade-off between confidentiality and throughput is an active area of research, with teams like Zama and Cypher racing to improve efficiency without compromising on security guarantees.
Despite these technical headwinds, the ecosystem’s momentum is unmistakable. Major EVM chains and rollup platforms are experimenting with FHE-powered modules for private DeFi liquidity pools, encrypted NFT metadata, and even cross-chain confidential messaging. As composability remains a core tenet of Ethereum’s success, the ability to plug privacy-preserving smart contracts into existing dApps, without sacrificing interoperability or regulatory compliance, marks a watershed moment for the industry.
How Developers Are Building With FHE Today
The developer experience is evolving rapidly. Thanks to frameworks like fhEVM and Cypher’s FHE-EVM Layer, Solidity developers can now integrate encrypted data types and logic directly into their smart contracts with minimal friction. Tools abstract away the underlying cryptography so teams can focus on business logic rather than security engineering.
Here’s what the workflow typically looks like for building encrypted smart contracts privacy solutions:
Steps to Develop Confidential EVM Smart Contracts with FHE
-
1. Set Up the FHE-Enabled Development EnvironmentBegin by installing the fhEVM framework by Zama or similar FHE-EVM solutions like Cypher’s FHE-EVM Layer. This provides the necessary libraries, encrypted data types, and tooling to build confidential smart contracts on EVM-compatible chains.
-

2. Define Encrypted Data Types in Your Smart ContractUtilize encrypted primitives such as euint64, euint32, and ebool within your Solidity code. These types, provided by fhEVM and Cypher’s FHE-EVM, allow for secure storage and operations on encrypted data directly on-chain.
-
3. Implement FHE Operations for Confidential ComputationUse FHE-specific functions like TFHE.add, TFHE.sub, and TFHE.mul to perform arithmetic and logical operations on encrypted values. This ensures that all computations remain confidential and never reveal plaintext data.
-
4. Integrate Secure Key Management ProtocolsLeverage threshold Multi-Party Computation (MPC) networks, such as those in Zama’s Confidential Blockchain Protocol, for FHE key generation and rotation. This guarantees that decryption keys are never exposed, maintaining end-to-end data confidentiality.
-
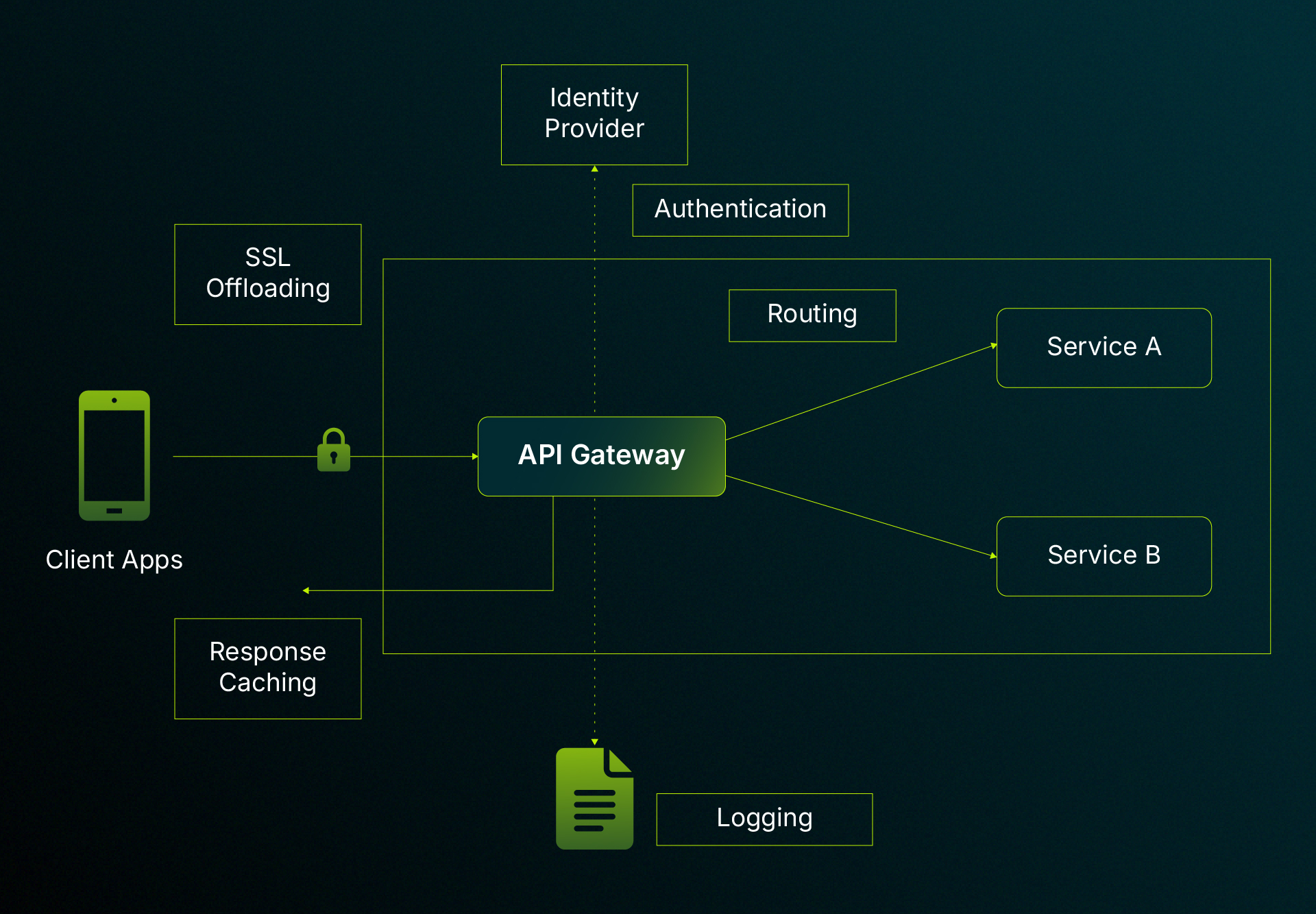
5. Utilize Coprocessors and Gateways for Off-Chain FHE ComputationFor complex or resource-intensive encrypted computations, use decentralized coprocessors and gateways (as in Zama’s architecture) to process data off-chain. These services validate encrypted inputs, manage access control, and securely return results to the main chain.
-
6. Deploy and Test the Confidential Smart Contract on an EVM-Compatible BlockchainDeploy your contract to a supported EVM chain, such as Ethereum or a testnet with fhEVM integration. Thoroughly test encrypted data flows, computation correctness, and privacy guarantees using provided developer tools.
With these advancements, projects ranging from private lending protocols to decentralized identity management are emerging. They’re leveraging FHE’s unique properties to offer users complete control over what information they reveal, and when.
What’s Next for Confidential EVM Chains?
The next phase of adoption will likely revolve around scalability and user experience. Expect continued improvements in coprocessor speed, key rotation latency, and developer tooling. Interoperability standards are also being discussed within privacy-focused working groups to ensure that confidential contracts can interact trustlessly across different EVM networks.
As regulators worldwide tighten requirements around data protection and consumer privacy, organizations running on public blockchains will increasingly turn to fully homomorphic encryption as a compliance enabler, not just a technological curiosity. The ability to prove regulatory conformity without revealing sensitive business data could become a decisive competitive advantage in sectors like finance, healthcare, and supply chain management.
Smart risk is the foundation of smart contracts: By embedding robust privacy at the protocol level using FHE, developers can offer users new assurances against surveillance capitalism, and unlock fresh markets where confidentiality is non-negotiable.
If you’re ready to explore how fully homomorphic encryption can transform your approach to blockchain privacy, or want a deeper dive into real-world architectures, visit our comprehensive guide at How Fully Homomorphic Encryption (FHE) Enables True Confidential Smart Contracts on EVM Chains.






