
Privacy is the lifeblood of next-gen decentralized finance. As DeFi explodes in popularity, the need to shield user data and transaction logic from prying eyes has never been greater. Enter encrypted smart contracts – the game-changing tech that’s rewriting the rules for confidential DeFi transactions. If you’re a developer, enterprise, or privacy-first user, buckle up: we’re about to break down how to actually implement these contracts and unlock a new era of secure blockchain protocols.

Why Traditional Blockchains Fail at Privacy
Standard blockchains like Ethereum are marvels of transparency, but that’s a double-edged sword. Every transaction, balance, and contract state is visible to anyone with an internet connection. For traders, institutions, and everyday users dealing with sensitive financial data, this is unacceptable. The answer isn’t to abandon blockchain; it’s to evolve it.
- Front-running attacks thrive on public mempool data.
- Business logic leaks can destroy competitive advantage.
- User privacy is sacrificed for auditability.
The solution? Confidential smart contracts that keep your logic and data encrypted end-to-end while still leveraging the trustless security of blockchain.
The Tech Stack: FHE vs TEE for Confidential DeFi Transactions
The two leading approaches for encrypted contract implementation are Fully Homomorphic Encryption (FHE) and Trusted Execution Environments (TEEs). Each comes with unique trade-offs for developers and users:
FHE vs TEE: Privacy Solutions for Smart Contracts
-

Fully Homomorphic Encryption (FHE): Enables computations directly on encrypted data, ensuring end-to-end privacy without revealing sensitive information at any stage. Platforms like Zama’s fhEVM bring FHE to Ethereum-compatible smart contracts, allowing developers to use familiar tools like Solidity for confidential DeFi applications.
-

Trusted Execution Environments (TEE): Uses secure, isolated hardware enclaves within processors to protect data during execution. Solutions such as Secret Network leverage TEEs to run privacy-preserving smart contracts, ensuring that nodes can verify transactions without accessing private data.
-
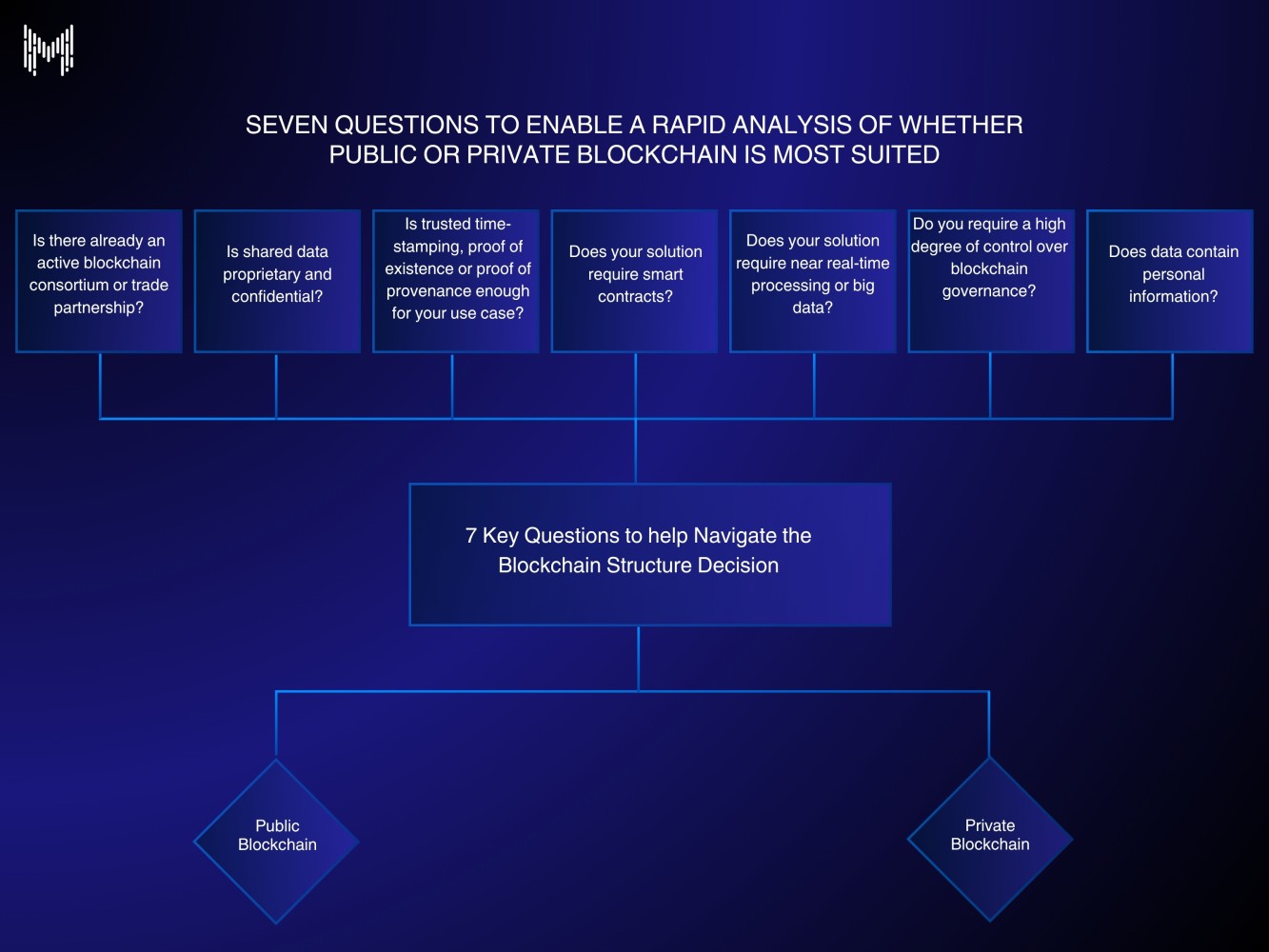
On-Chain vs. Off-Chain Confidentiality: FHE keeps all computations and encrypted data on-chain, maximizing decentralization and transparency. TEEs typically process data off-chain within secure hardware, then relay results back to the blockchain.
-
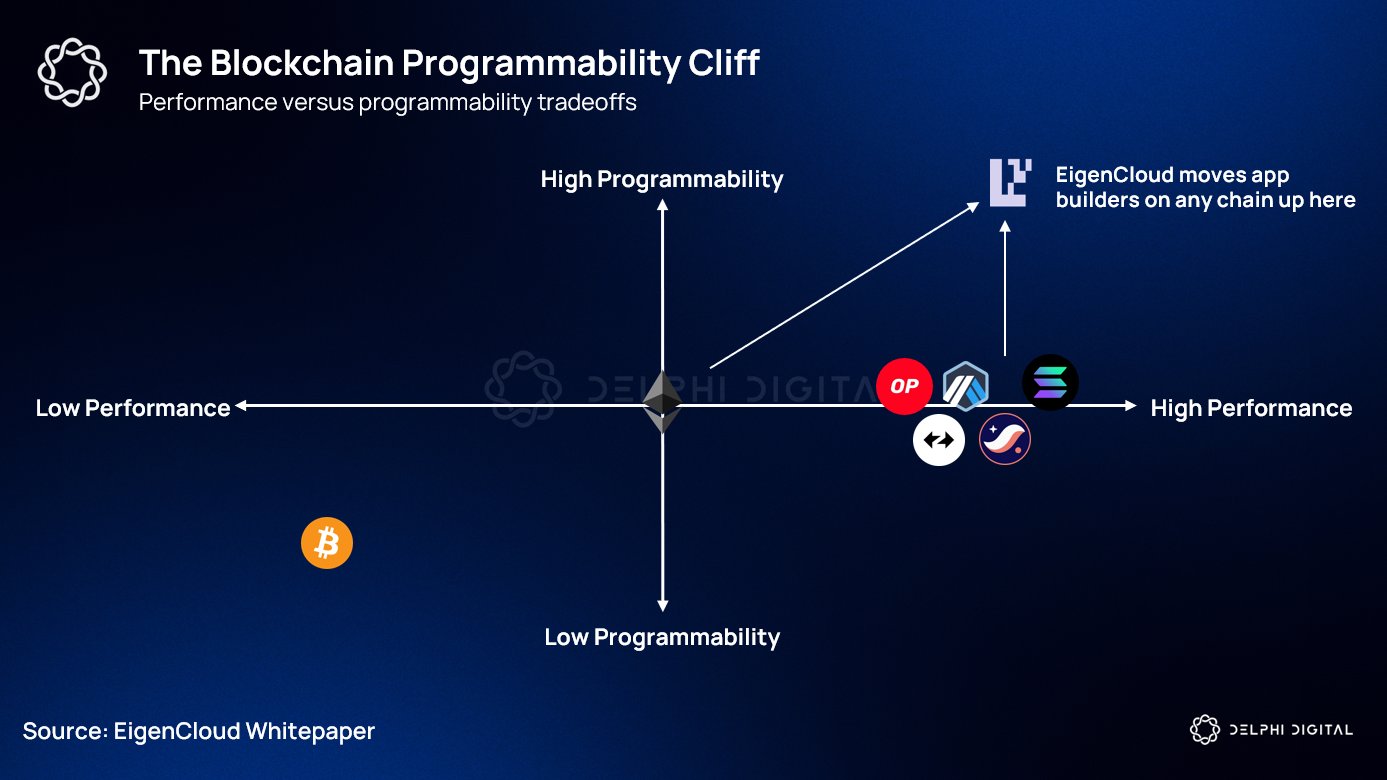
Performance and Scalability: FHE is computationally intensive, which can impact transaction speeds, but ongoing advancements (like Zama’s coprocessor) are addressing these challenges. TEEs generally offer faster execution but rely on the security of specific hardware vendors.
-

Security and Trust Assumptions: FHE relies on mathematical cryptography, minimizing the need to trust third parties. TEEs require trust in hardware manufacturers and enclave integrity, which can be a concern if vulnerabilities are discovered.
Fully Homomorphic Encryption (FHE):
- No decryption required: All computations happen directly on encrypted data.
- Zama’s fhEVM: Lets you write Solidity smart contracts that process encrypted inputs/outputs natively on Ethereum-compatible chains.
- Main benefit: Maximum privacy without relying on specialized hardware or trusted parties.
Trusted Execution Environments (TEEs):
- Hardware-isolated computation: Code runs in a secure enclave inside each node’s processor (e. g. , Intel SGX).
- Secret Network: Executes smart contracts where validators can verify results without accessing raw data.
- Main benefit: High performance and mature tooling; ideal for complex DeFi dApps needing low latency.
Banks, trading desks, DAOs, everyone can now transact privately on-chain without sacrificing decentralization or composability. That’s revolutionary!
Your Roadmap: Implementing Encrypted Smart Contracts Step by Step
If you’re ready to build the future of privacy in DeFi, here’s your battle plan for deploying encrypted smart contracts:
- Select your platform:
- If you want pure cryptographic privacy with no hardware dependencies, go with Zama’s fhEVM or similar FHE-based solutions.
- If performance is key (think high-frequency trading), consider Secret Network or other TEE-powered blockchains.
- Create your confidential contract logic:
- Zama provides Solidity-compatible libraries so you can encrypt inputs/outputs without being a crypto PhD. TEEs offer Rust/CosmWasm SDKs for building secret contracts fast.
- Pilot on testnet:
- This isn’t optional! Simulate real-world usage and confirm that no sensitive info leaks, not even in logs or error messages!
- Mainnet deployment and monitoring:
- Your work isn’t done after launch. Monitor contract activity for anomalies and stay current with security patches as both FHE and TEE tech rapidly evolve.
Let’s be real: privacy isn’t a one-and-done upgrade. It’s a discipline that demands vigilance, iteration, and a willingness to push boundaries. Once your encrypted smart contracts are live, the work shifts to robust monitoring and continuous improvement. The pace of cryptography and DeFi innovation means today’s best practices can become tomorrow’s vulnerabilities if you’re not proactive.
Best Practices for Maintaining Confidential DeFi Contracts
- Routine audits: Engage with security researchers who understand both FHE and TEE architectures. Don’t settle for surface-level reviews; demand deep dives into your contract logic and encryption flows.
- Upgrade regularly: Both Zama’s fhEVM and Secret Network release frequent updates as new cryptographic primitives emerge. Stay ahead of the curve by upgrading dependencies and following their changelogs.
- Community engagement: Tap into open-source communities to crowdsource bug bounties, share anonymized attack data, and learn from others building privacy-first DeFi apps.
- Disaster planning: Even the best code can have unknown flaws. Design upgrade paths and emergency pause mechanisms that don’t compromise confidentiality if a critical vulnerability is discovered.
The reward? You’re not just protecting users, you’re building a foundation for institutional DeFi adoption, where privacy is non-negotiable.
Real-World Use Cases: Where Encrypted Smart Contracts Shine
- Private lending and borrowing: Lenders can assess risk using encrypted credit scores or collateral without exposing user identities or positions.
- Confidential order books and auctions: Prevent front-running and MEV by keeping bids sealed until execution time. (For an in-depth look at this use case, see how confidential smart contracts enable private DeFi order books)
- Sensitive business agreements: Enterprises can automate NDAs or revenue-sharing deals on-chain without leaking proprietary information, unlocking new forms of trustless B2B collaboration.
The bottom line: encrypted contract implementation isn’t just about privacy, it’s about unlocking entirely new markets that were previously impossible on transparent blockchains.
Challenges and What’s Next for Privacy in DeFi
No tech is perfect out of the gate. Developers face genuine challenges with encrypted smart contracts: higher computational costs (especially with FHE), UX trade-offs around transaction speed, and a learning curve integrating novel SDKs into legacy stacks. But momentum is building fast, Zama’s partnership with OpenZeppelin has accelerated audited tooling, while Secret Network continues to onboard mainstream dApps thanks to its mature TEE infrastructure.
Top Obstacles in Encrypted Smart Contract Development
-
Complexity of Homomorphic Encryption (FHE) Integration: Implementing Zama’s fhEVM or similar FHE solutions in smart contracts requires developers to adapt to new cryptographic paradigms, making coding, debugging, and optimization significantly more challenging than with standard Solidity.
-
Performance Overhead and Scalability: Confidential computing methods like FHE and Secret Network’s TEEs introduce additional computational overhead, which can slow down transaction processing and impact the scalability of DeFi applications.
-

Limited Tooling and Ecosystem Support: Compared to traditional Ethereum development, the ecosystem for encrypted smart contracts is still maturing, with fewer libraries, debugging tools, and community resources available for platforms like fhEVM and Secret Network.
-
Ensuring End-to-End Data Confidentiality: Developers must ensure that sensitive data remains encrypted not only during computation but also at every step of the transaction lifecycle, including storage and transmission, which adds layers of security complexity.
-

Cross-Platform Compatibility and Interoperability: Integrating encrypted smart contracts with existing DeFi protocols and oracles, especially across platforms like Ethereum, Zama, and Secret Network, poses significant interoperability challenges.
-

Auditing and Security Verification: Traditional smart contract auditing tools are not fully equipped to analyze encrypted logic, making it harder to verify the security and correctness of confidential smart contracts.
If you’re serious about scaling confidential DeFi transactions, focus on composability, ensure your private contracts can still interact with other protocols securely. And never underestimate the power of community-driven standards; as more projects adopt privacy-first architectures, interoperability will become smoother and more robust for everyone.
This is your call to action: don’t let yesterday’s limitations dictate tomorrow’s opportunities. Whether you’re building the next billion-dollar protocol or simply want to trade privately without compromise, now is the time to master encrypted smart contract deployment.
Your edge in this market comes from knowledge, and bold execution.










