Building a confidential ERC20 token with Fully Homomorphic Encryption (FHE) is a transformative step for privacy on EVM-compatible blockchains. Developers and enterprises can now create tokens where balances and transactions are not just pseudonymous, but cryptographically concealed from the public, while still enabling on-chain computation. This is possible thanks to recent advances in FHE, which allows computations on encrypted data without ever exposing the underlying values.
How FHE Reinvents ERC20 Token Privacy
Fully Homomorphic Encryption enables smart contracts to process encrypted integers, so sensitive information like token balances and transfer amounts remain hidden, even from network validators. Unlike zero-knowledge proofs, which reveal only the validity of a statement, FHE allows actual arithmetic on encrypted data. This breakthrough is now accessible to Ethereum developers through platforms such as Zama’s fhEVM, which brings FHE computation directly to the EVM layer.
With this technology, confidential ERC20 tokens can be deployed on any EVM chain, including Ethereum, Polygon, and Arbitrum, without requiring changes to the underlying blockchain. This flexibility is crucial for DeFi protocols and enterprises seeking to protect user data while maintaining interoperability.
Key Components for Confidential ERC20 Tokens
To implement a confidential ERC20 token, several architectural changes are necessary compared to standard tokens:
Essential Features for Confidential ERC20 Tokens with FHE
-

Encrypted Balances and Transactions: All token balances and transaction amounts must be stored and processed as encrypted values using FHE, ensuring privacy even during computation. This approach is supported by frameworks like Inco Network’s Confidential ERC-20 Framework.
-
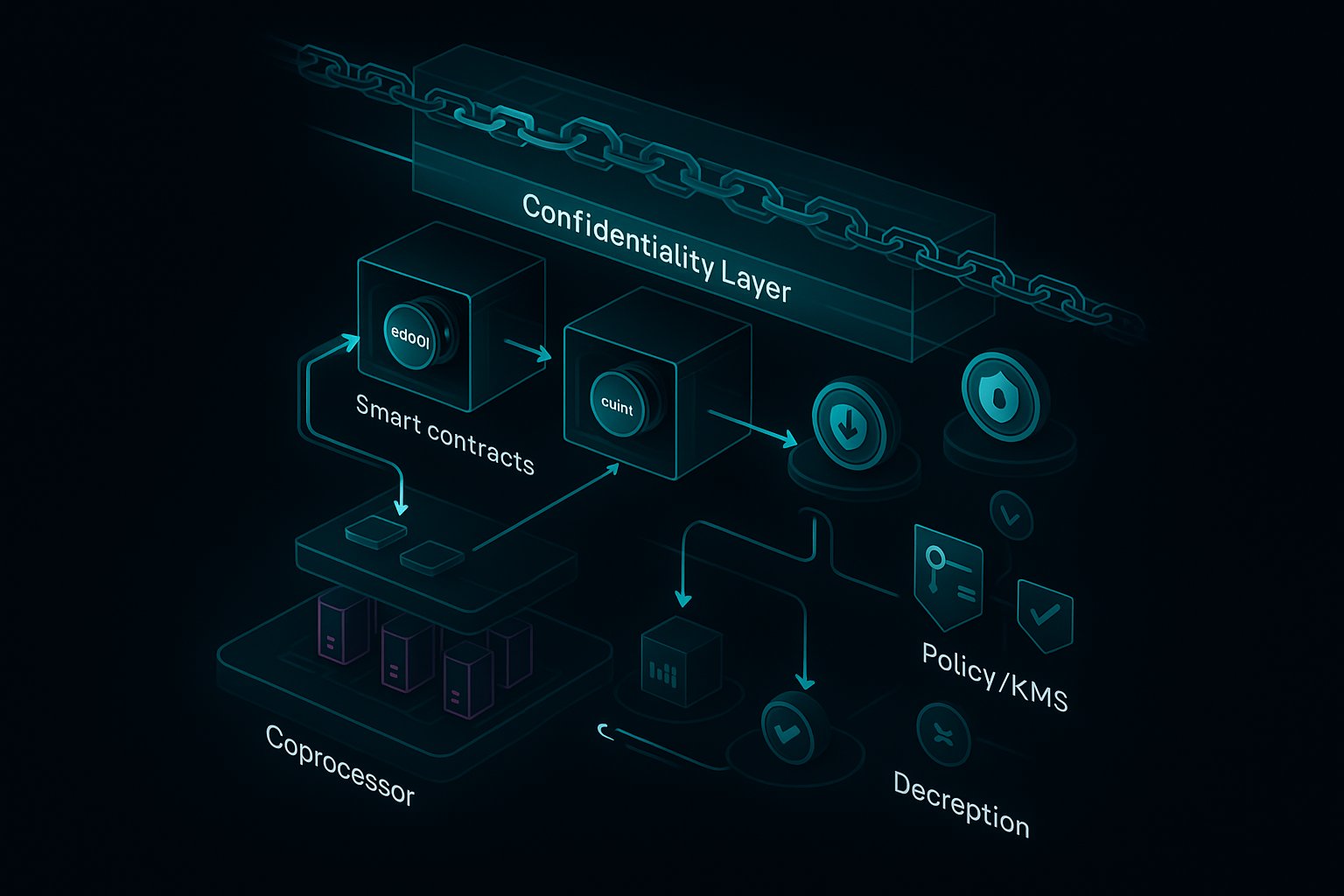
FHE Integration with EVM: The smart contract platform must support FHE operations natively or via coprocessors, enabling confidential computation on encrypted data. Zama’s fhEVM exemplifies such integration for Ethereum-compatible chains.
-
Compatibility with Standard ERC-20 Infrastructure: Confidential tokens should maintain interoperability with existing wallets, dApps, and DeFi protocols by adhering to ERC-20 standards, as seen in OpenZeppelin’s Confidential Fungible Token standard.
-
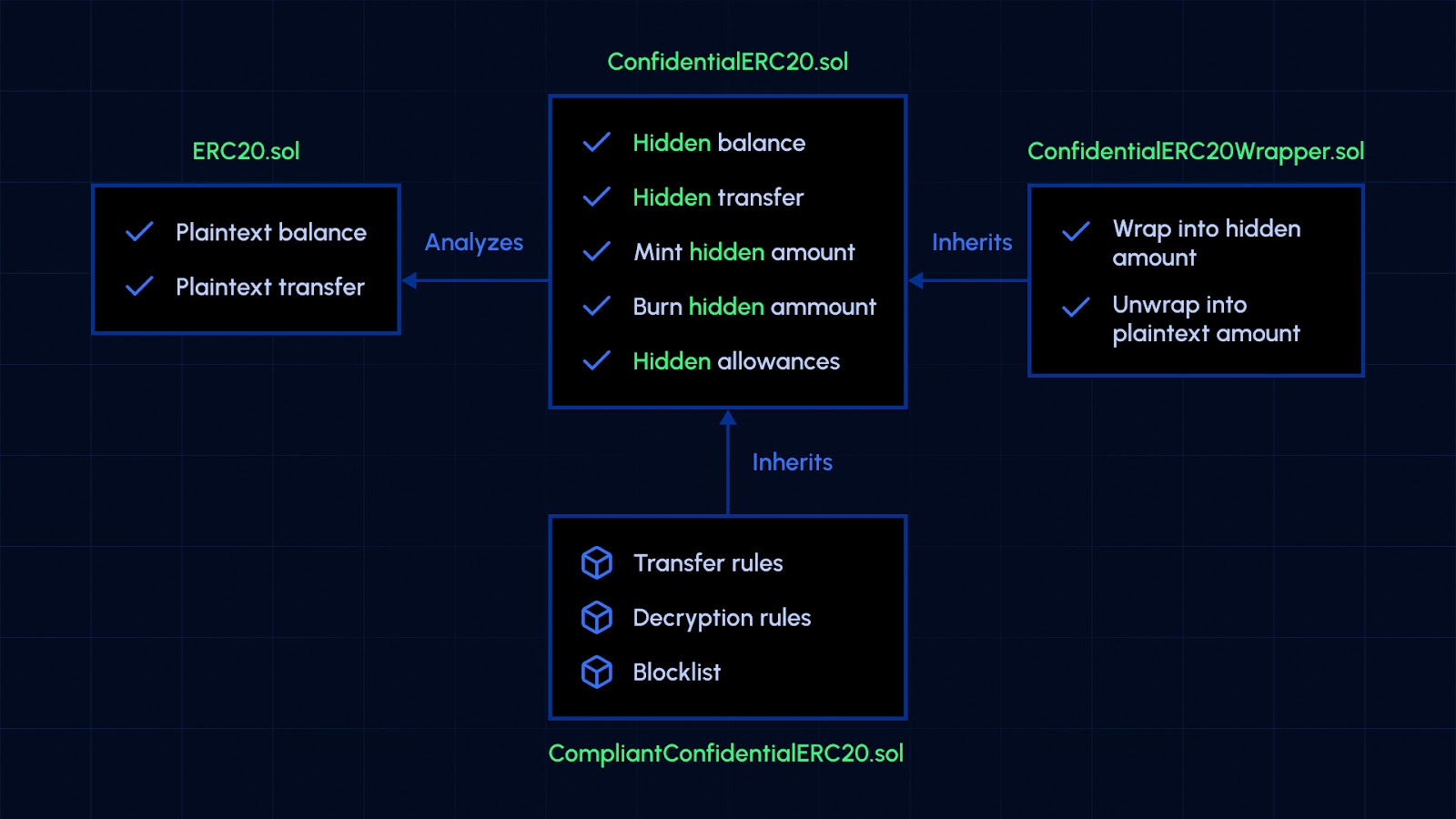
Delegated Viewing for Compliance: Implement mechanisms that allow authorized third parties to view encrypted balances and transactions when required for regulatory compliance, as highlighted in Circle’s Confidential ERC-20 Framework.
-
Efficient FHE Operations: Use optimized FHE schemes like TFHE for practical performance, minimizing latency and computational overhead in confidential transactions, as discussed in Ethereum Research.
-

Comprehensive Testing and Deployment Tools: Leverage established tools such as Hardhat, Foundry, and Remix for deploying and testing confidential ERC-20 contracts on EVM-compatible testnets, as recommended by Zama and Inco.
At the core, balances are stored as encrypted integers, often using types like euint256 (encrypted 256-bit unsigned integers) provided by frameworks such as Inco’s Confidential ERC20 Framework. Token transfers and approvals are handled through functions that operate on encrypted values, ensuring that neither the contract nor observers can discern the actual amounts.
Compatibility is also maintained with existing ERC20 infrastructure, so wallets and DeFi platforms can interact with confidential tokens using familiar interfaces. However, additional mechanisms are introduced for delegated viewing, allowing regulated access for compliance without undermining privacy for regular users.
Frameworks and Tools: Accelerating Confidential Token Development
The ecosystem around confidential smart contracts is rapidly maturing. Developers can leverage open-source frameworks such as:
- Zama’s fhEVM: Provides EVM-compatible FHE computation primitives (details here).
- OpenZeppelin Confidential Token Standard: Offers modular contracts for encrypted token balances (see docs).
- Inco Network’s Confidential ERC20 Framework: Transforms standard tokens into confidential versions with optional delegated viewing (source code).
These tools enable developers to focus on business logic and user experience rather than cryptographic implementation details. For hands-on guidance, tutorials like “How To Create a Confidential Token” by Inco demonstrate step-by-step deployment on testnets such as Base Sepolia.
Why Performance and Compliance Matter
While FHE unlocks unprecedented privacy, developers must be aware of its computational demands. Encrypted operations are more resource-intensive than plaintext ones, which may impact throughput and latency. Regulatory compliance is also essential; frameworks often include delegated viewing keys so authorized auditors can access transaction details when required.
This foundation sets the stage for building robust, scalable, and privacy-preserving tokens that meet both user expectations and regulatory requirements.
To optimize performance, developers should benchmark encrypted token operations in realistic environments. Several projects, including Inco’s Confidential ERC20 Framework, provide test suites and simulation tools to profile gas usage and latency under varying loads. It’s also important to consider the impact of FHE on transaction fees, as more complex computations may increase costs compared to standard ERC20 transfers.
Security remains paramount. The use of FHE should not introduce new attack surfaces. Rigorous auditing, both at the smart contract and cryptographic protocol level, is essential. Leveraging widely adopted libraries such as OpenZeppelin’s confidential contracts helps mitigate risks by building on peer-reviewed codebases.
Deployment, Testing, and Real-World Integration
After developing your confidential ERC20 contract, deploy it to a testnet like Base Sepolia or Goerli for initial validation. Use established tools such as Hardhat or Foundry for deployment scripting, and Remix for live debugging. Comprehensive testing should include:
- Verifying that encrypted balances update correctly after transfers
- Ensuring delegated viewing functions only reveal data to authorized parties
- Testing integration with wallets and DeFi protocols for seamless UX
Once validated, mainnet deployment becomes a straightforward process, with frameworks supporting any EVM-compatible chain. Keep in mind that user education is critical, wallets must clearly indicate when balances are confidential and provide intuitive flows for managing viewing keys or permissions.
The Path Forward: Use Cases and Future Potential
The advent of confidential ERC20 tokens unlocks compelling applications across decentralized finance (DeFi), institutional asset management, payroll, gaming, and beyond. For example, DeFi protocols can now offer privacy-preserving swaps and lending without exposing user positions. Enterprises benefit from on-chain compliance audits without leaking sensitive business data.
Looking ahead, research into FHE-optimized rollups and coprocessors promises to further scale privacy solutions for mass adoption. Initiatives like Zama’s fhEVM coprocessor are already enabling confidential computation across chains without requiring protocol-level changes (learn more here).
For developers eager to explore this frontier, open-source projects and community-led tutorials provide a low barrier to entry. Experimentation is encouraged, whether you’re wrapping an existing ERC20 token in confidentiality or designing a novel privacy-first protocol.
Pro tip: When implementing encrypted token balances, use types like
euint256for compatibility with FHE frameworks. Always separate logic that handles encryption from business rules to maintain clarity and security.
The landscape is evolving quickly, but one truth remains: robust privacy tooling is essential for mainstream adoption of blockchain technology. By leveraging FHE smart contracts today, you help set the standard for tomorrow’s secure and compliant crypto economy.