In the high-stakes arena of decentralized finance, where every transaction lays bare user positions and strategies, true privacy remains an elusive prize. Enter Fully Homomorphic Encryption (FHE)-enabled smart contracts on Base and Arbitrum: a game-changer for confidential smart contracts Base Arbitrum deployments. Fhenix’s CoFHE coprocessor now bridges this gap, letting developers wield Solidity to craft FHE encrypted smart contracts that compute on encrypted data without ever exposing it. This isn’t just theoretical; it’s live on Sepolia testnets for Ethereum, Arbitrum, and Base, paving the way for privacy-preserving DeFi contracts that shield balances, orders, and logic from prying eyes.
Why FHE Redefines Blockchain Privacy for L2 Developers
Fully Homomorphic Encryption stands apart from zero-knowledge proofs or off-chain mixing by allowing computations directly on ciphertexts. Imagine a lending protocol where collateral values, interest rates, and borrower identities stay encrypted end-to-end; the blockchain sees only noise, yet the contract executes flawlessly. Fhenix integrates this into EVM-compatible chains via CoFHE, their encrypted compute layer. For homomorphic encryption blockchain developers, this means no custom VMs or gas-warping wrappers, just familiar Solidity with FHE primitives.
On Base and Arbitrum, low fees amplify FHE’s viability. These optimistic rollups handle the compute overhead without Ethereum mainnet’s punishing costs, making Fhenix FHE Solidity tutorial workflows practical for real DeFi apps. OpenZeppelin’s Confidential Token standard, born from their Zama partnership, mirrors ERC-20 but encrypts balances and transfers. Vulnerabilities like reentrancy or oracle manipulation? Mitigated when states remain opaque. My two decades in markets affirm: in DeFi, opacity isn’t evasion; it’s strategic defense against front-running and MEV predators.
Configuring Your Environment for FHE Contract Development
Deployment starts with precision setup. Fhenix’s docs outline a streamlined path, but prudence demands verification at each step. Install Foundry for Solidity compilation, then the CoFHE SDK for encryption ops. Fund testnet wallets on Sepolia variants, Arbitrum Sepolia and Base Sepolia faucets are reliable. Node providers like Alchemy or Infura suffice, but prioritize those with L2 support to avoid RPC lags during FHE-heavy simulations.
This checklist ensures you’re battle-ready. I’ve seen devs falter on key generation alone; Fhenix simplifies it with CLI tools that output public/private keypairs for contract encryption. Test locally first, CoFHE’s anvil fork emulates FHE ops, letting you iterate without testnet spam.
Drafting Your Inaugural FHE-Enabled Contract
With environment primed, dive into code. Fhenix provides fhERC-20 templates: extend them for tokens where balances encrypt natively. Logic like transfers or approvals operates on ciphertexts; users submit encrypted inputs, the contract homomorphically processes, and outputs stay sealed until client-side decryption.
This snippet captures the essence: import Fhenix libraries, declare states as FheUint (encrypted integers), and wrap ops in euint calls. Compile with Foundry, targeting CoFHE-enabled chains. Deploy scripts handle encryption keys; inject your public key during init. Opinion: Skip vanilla ERC-20 upgrades, embrace fhERC-20 from the ground up for seamless confidentiality. Next, simulate interactions: encrypt inputs via JS SDK, call the contract, decrypt outputs. Pitfalls? Gas estimation, FHE ops inflate it 10-50x, so optimize with batching.
Arbitrum’s sequencer speed shines here, batching FHE proofs efficiently, while Base’s OP Stack keeps costs under a cent per tx even loaded. For DeFi primitives like AMMs, encrypt reserves and compute shares homomorphically; liquidity providers revel in hidden positions, deterring sandwich attacks.
Transitioning from simulation to live deployment demands a methodical approach, especially with FHE’s computational heft. Base Sepolia, leveraging Optimism’s stack, offers sub-cent fees ideal for iterative testing, while Arbitrum Sepolia’s optimistic model accelerates confirmations. Both support CoFHE via standard RPC endpoints, but chain-specific configs prevent common pitfalls like fork mismatches.
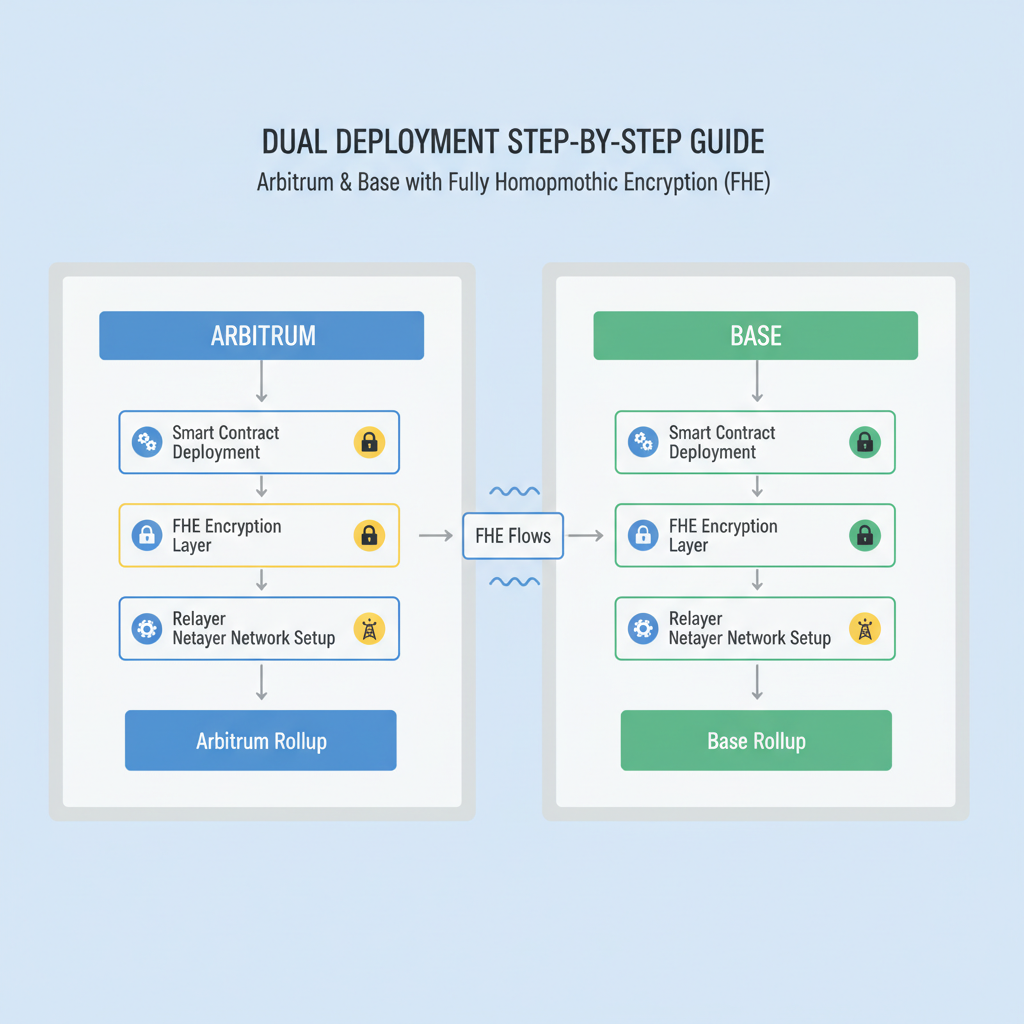
Step-by-Step Deployment to Base and Arbitrum Testnets
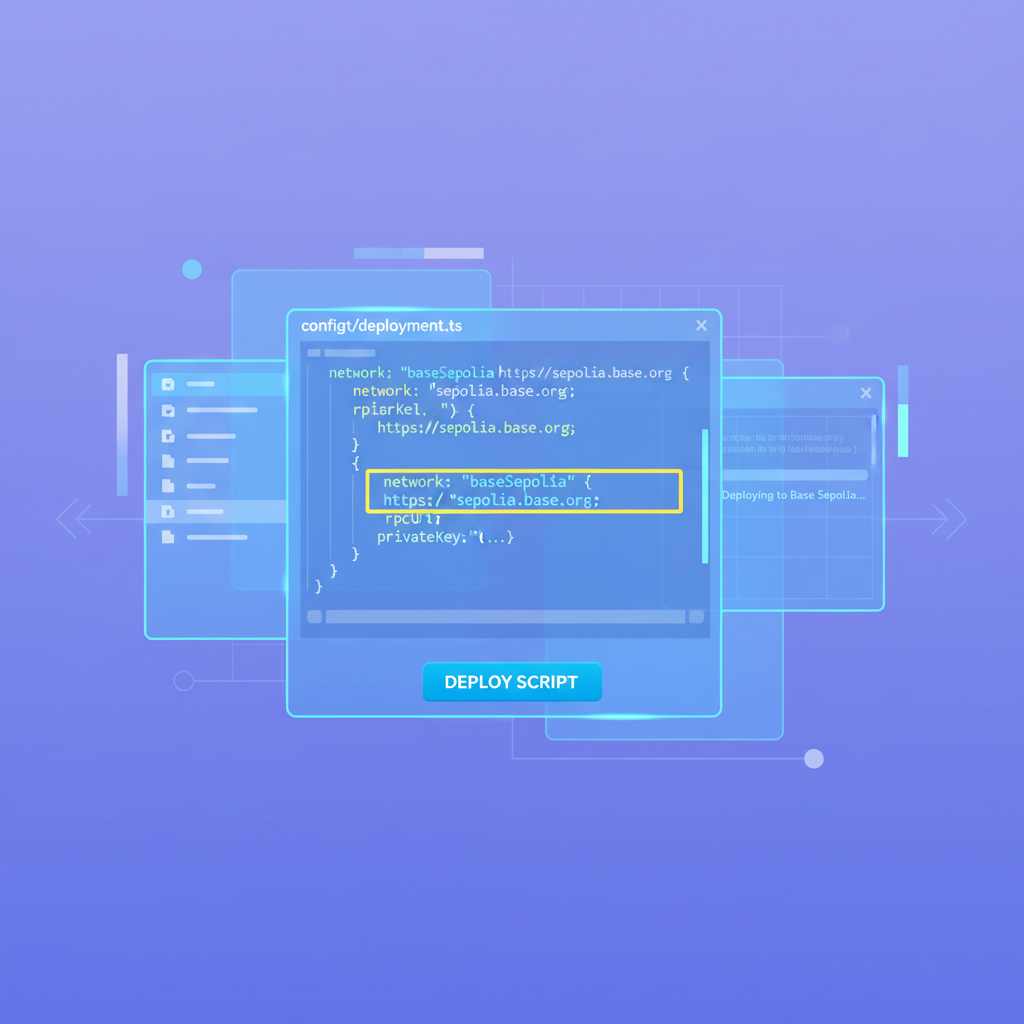
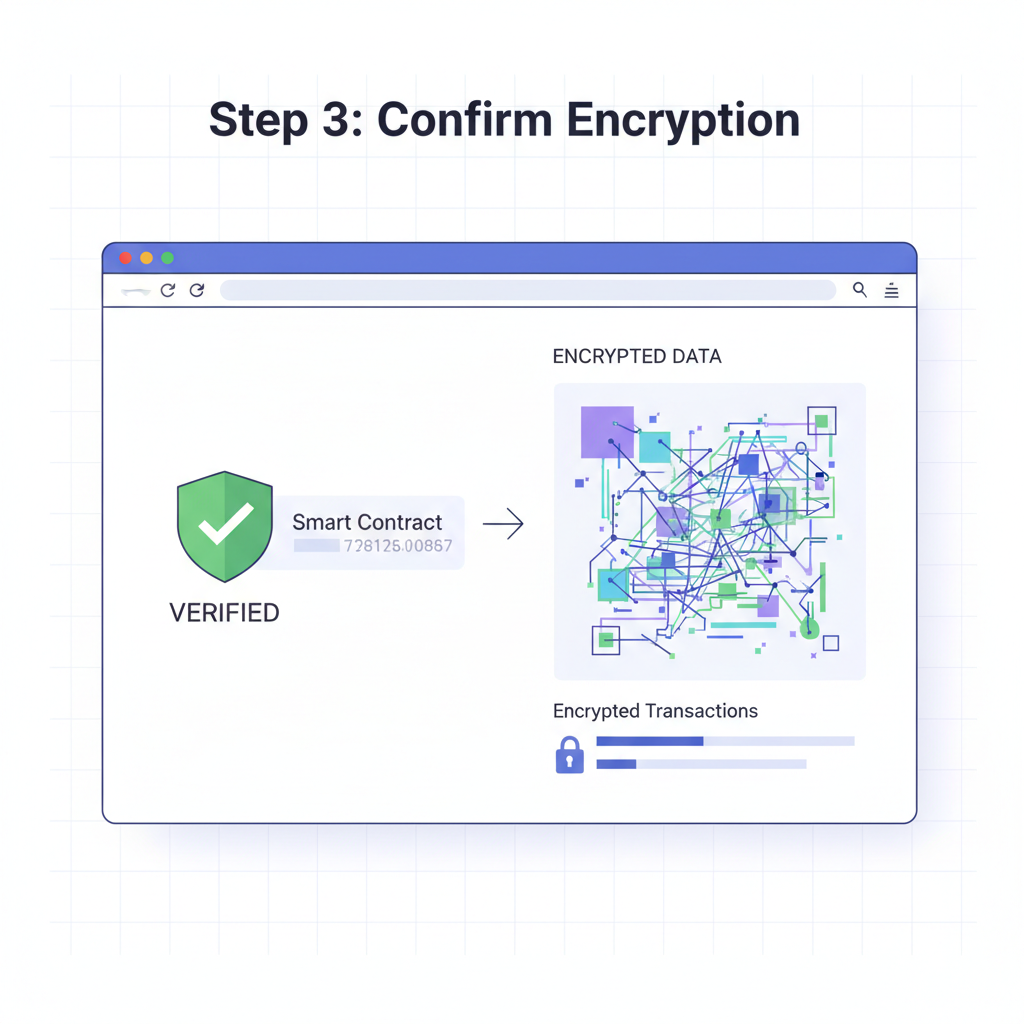
Follow this guide meticulously; I’ve deployed dozens of privacy prototypes, and chain ID errors alone waste hours. Start with forge create scripted for each network: set RPC URLs from Alchemy (Base: sepolia. base. org, Arbitrum: sepolia. arbitrum. io), inject your encryption public key, and estimate gas with --estimate-gas. Fhenix’s CLI automates key management, generating FhePubKey on-chain during constructor. Post-deployment, verify via Etherscan equivalents: Base Sepolia explorer and Arbiscan Sepolia confirm bytecode, but inspect events for encryption init success.
For confidential smart contracts Base Arbitrum, multi-chain scripts shine. Use Foundry’s broadcasting: one command deploys to both, broadcasting transactions in parallel. Opinion: Prioritize Base for cost-sensitive prototypes, Arbitrum for throughput-heavy apps like confidential order books. Gas refunds on L2s offset FHE premiums, often netting under $0.05 total.
This script exemplifies prudence: environment variables mask keys, vm. startBroadcast handles multi-chain, and custom verifiers log tx hashes. Execute with forge script DeployFHE. s. sol --rpc-url $BASE_RPC --private-key $PK --broadcast. Monitor via tender. ly for simulations pre-live.
Security Imperatives and Optimization Tactics
Deployment’s thrill fades without ironclad security. OpenZeppelin’s FHEVM guide is non-negotiable: audit encryption patterns, guard against malleability in homomorphic ops, and implement client-side decryption guards. Common traps? Overflow in euint arithmetic, sidestepped by bounded checks; rekeying exposures, averted with ephemeral keys per session. For privacy-preserving DeFi contracts, integrate fhERC-20’s access controls, ensuring only keyholders decrypt states.
Optimization elevates viability. Batch FHE operations to slash gas 30-40%; use Fhenix’s compression libs for ciphertexts. Profile with Foundry traces: forge test --gas-report flags hotspots. On Arbitrum, leverage blob storage for proofs; Base’s pipeToL1 batches efficiently. My strategy: prototype on local anvil, stress-test on testnet, mainnet only post-audit. Zama-OpenZeppelin standards future-proof against evolving threats.
Real DeFi wins emerge here: confidential lending where overcollateralization ratios compute blindly, blind auctions shielding bids, perpetuals hiding leverage. Fhenix’s roadmap hints mainnet soon, but testnets suffice for MVPs. Developers mastering this wield a competitive edge in a transparent arena begging for shadows.
Patience yields: iterate deployments, refine logic, and scale to production. In blockchain’s privacy frontier, FHE on Base and Arbitrum isn’t a novelty; it’s the prudent path to enduring DeFi dominance.