
As quantum computing edges closer to practical reality, the foundations of blockchain security face an existential challenge. Current cryptographic protocols, relied upon by platforms like Bitcoin and Ethereum, hinge on mathematical problems that quantum algorithms such as Shor’s can shatter in minutes. For encrypted smart contracts quantum enthusiasts and developers, this means confidential transactions could be retroactively exposed, undermining trust in decentralized finance. Transitioning to quantum resistant smart contracts isn’t optional; it’s a strategic imperative to preserve blockchain quantum security.
Unpacking the Quantum Vulnerability in Legacy Cryptography
Public-key cryptography underpins every signature and key exchange in blockchains. Elliptic Curve Digital Signature Algorithm (ECDSA), the workhorse of Ethereum and Bitcoin, succumbs to quantum attacks via Shor’s algorithm, which efficiently solves the discrete logarithm problem. Hash functions like SHA-256 fare better against Grover’s algorithm but still suffer quadratic speedups, potentially compromising proof-of-work integrity. Deloitte’s quantitative analysis highlights Ethereum’s exposure: a sufficiently powerful quantum machine could forge signatures across historical transactions, eroding immutability.
ScienceDirect research navigates this threat landscape, emphasizing how blockchains’ reliance on these primitives invites disruption. Fireblocks outlines evolutionary paths, from hybrid consensus to cryptographic overhauls. Yet, most chains cling to pre-quantum signatures due to their compactness; Reddit discussions note quantum-resistant alternatives balloon transaction sizes by 100-1000x, clogging networks. My view? This inertia is a calculated risk, betting on quantum delays, but savvy enterprises can’t afford such gambles in privacy preserving smart contracts quantum.
Key Quantum Threats to Blockchain
-
ECDSA Breakage via Shor’s Algorithm: Shor’s algorithm efficiently solves the elliptic curve discrete logarithm problem (ECDLP), breaking ECDSA signatures used by Bitcoin and Ethereum (Sources: Fireblocks, Deloitte).
-

Hash Collision Risks from Grover’s Algorithm: Provides quadratic speedup for brute-force attacks, reducing security of SHA-256 hash functions in Bitcoin mining and Ethereum proofs (Sources: ScienceDirect, Rapid Innovation).
-
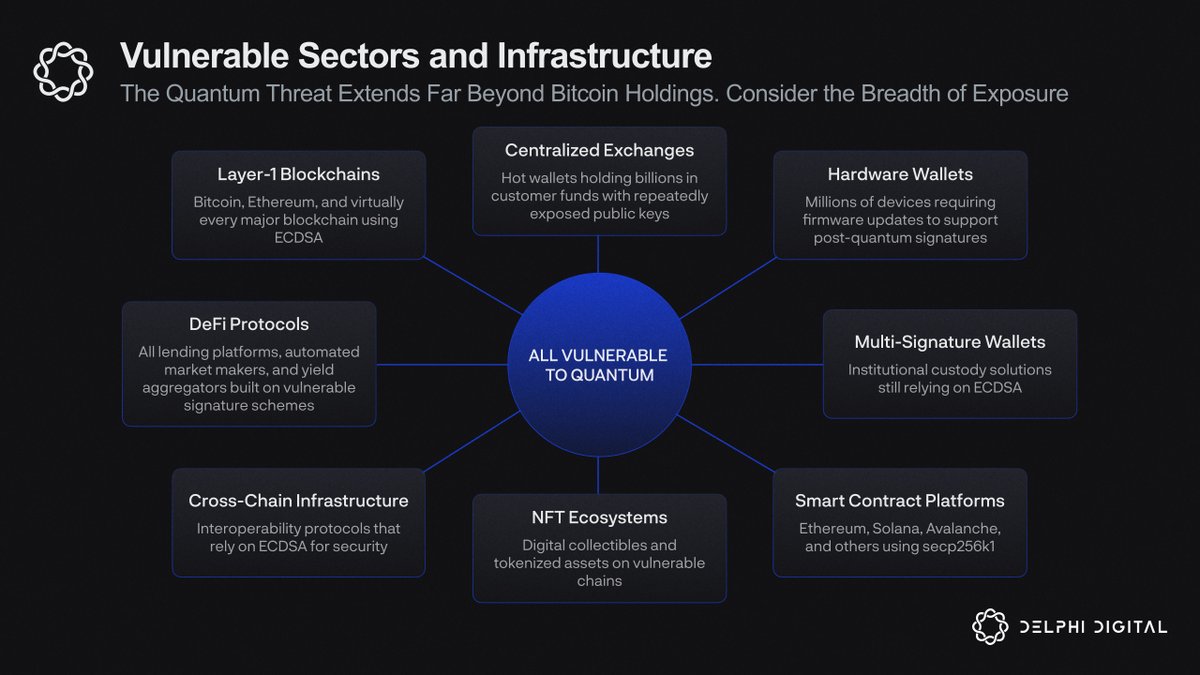
Impacts on Ethereum and Bitcoin Signatures: Enables transaction forgery and fund theft from exposed public keys, threatening core blockchain integrity (Sources: The Quantum Resistant Ledger, IDB Publications).
-
Size Challenges of Post-Quantum Alternatives: Signatures like Dilithium are 100-1000x larger than ECDSA, bloating transaction sizes which comprise ~2/3 of Bitcoin tx data (Sources: Reddit r/CryptoTechnology, OPastPublishers).
Post-Quantum Algorithms: The New Guardians of Smart Contracts
NIST’s standardization efforts have crowned lattice-based schemes like CRYSTALS-Dilithium and Kyber as frontrunners. Dilithium offers robust digital signatures resistant to quantum forgery, ideal for secure encrypted contracts ethereum. These algorithms leverage hard lattice problems, presumed safe even against quantum adversaries. Rapid Innovation defines quantum-resistant blockchains as those embedding such primitives from inception, avoiding painful migrations.
The Inter-American Development Bank warns of broader protocol threats, urging immediate audits. Nature’s exploration of quantum deep learning-enhanced Ethereum hints at synergies, where smart contracts validate data migrations securely. Opinionated take: while computationally heavier, these tools enable true confidentiality; traditional chains retrofitting them will lag, handing advantages to native quantum-safe platforms.
Pioneering Implementations in Quantum-Resistant Ecosystems[/h2>
QuantumPrivate. org leads with deployable contracts like QuantumToken, an ERC20 variant using Dilithium for privacy-enhanced transfers, and SecureMultiSig wallets. PrivateVoting employs zero-knowledge proofs atop post-quantum encryption, ensuring anonymous governance. These showcase lattice-based encryption safeguarding sensitive data, as OPast Publishers affirm: Dilithium bolsters integrity but demands optimized implementations to offset size penalties.
The Quantum Resistant Ledger (QRL) stands as a Layer-1 beacon, wielding XMSS signatures since launch. Wikipedia notes its exchange listings and ongoing vitality into 2025. Arxiv’s PQS-BFL framework merges ML-DSA signatures with smart contracts for federated learning verification, proving efficiency. zk-Agreements protocol fuses ZKPs and secure computation, balancing transparency with confidentiality in agreements. Here, creativity shines: developers blending these yield scalable, verifiable privacy without quantum dread.
Hybrid schemes, like Inspire HEP’s Python-blockchain interplay, further exemplify secure, verifiable interactions resistant to quantum eavesdroppers. These advancements aren’t theoretical; they’re deployable today, urging developers to prioritize quantum resistant smart contracts in their stacks.
Trade-Offs and Optimization Strategies for Deployment
Adopting post-quantum cryptography introduces hurdles: signature bloat strains bandwidth, and verification latency tests scalability. Reddit threads quantify this; Dilithium signatures dwarf ECDSA by orders of magnitude, potentially inflating Ethereum gas fees. Yet, optimizations abound. Layer-2 rollups can offload verification, while hash-based signatures like XMSS offer stateful alternatives with forward security. My analytical lens sees this as an engineering pivot: compress via aggregation schemes, as NIST trials suggest, or embrace specialized chains like QRL for native efficiency.
Privacy-preserving protocols amplify these gains. zk-Agreements demonstrates how zero-knowledge proofs mask terms in smart contracts, executed deterministically without revelation. PQS-BFL’s ML-DSA integration validates federated models decentrally, maintaining accuracy amid quantum threats. Enterprises eyeing encrypted smart contracts quantum must weigh these: upfront costs yield long-term resilience, outpacing laggards in blockchain quantum security.
Comparison of Post-Quantum Signature Schemes vs. ECDSA Baseline
| Signature Scheme | Public Key Size (bytes) | Signature Size (bytes) | Relative Sig. Size (vs. ECDSA) | Performance (relative to ECDSA) | Security Level | Notes |
|---|---|---|---|---|---|---|
| ECDSA | 33 (compressed) | 70 | 1x | 1x (baseline) | 128-bit classical | Pre-quantum baseline; vulnerable to quantum attacks (Shor’s algorithm) |
| Dilithium (CRYSTALS-Dilithium) | 1,312 | 2,420 | ~35x | 20-50x slower sign/verify | NIST Level 2 (128-bit PQ) | Stateless, lattice-based; used in SecureMultiSig contracts; larger sizes increase tx costs |
| XMSS | 67 | ~2,500 – 40,000 | ~35-600x | 50-200x slower | 256-bit classical (hash-based) | Stateful, forward secure; powers Quantum Resistant Ledger (QRL) |
| ML-DSA (e.g., ML-DSA-65) | 1,952 | 3,293 | ~47x | 20-50x slower sign/verify | NIST Level 3 (192-bit PQ) | ML-optimized lattice-based; used in PQS-BFL for federated learning |
Developer Roadmap: Building Quantum-Safe Confidential Transactions
Start with audits: scan legacy contracts for ECDSA exposure using tools like Slither adapted for quantum risks. Migrate incrementally; hybrid signatures bridge eras, signing new txs quantum-safe while honoring old. QuantumPrivate’s suite provides blueprints: fork QuantumToken for custom ERC20s with lattice encryption, or SecureMultiSig for wallets demanding multi-party thresholds.
Integrate ZK for confidentiality; PrivateVoting’s model hides votes yet proves validity, vital for DAOs. Opinion: forward-thinking protocols like zk-Agreements redefine agreements, automating escrow without leaks. Scale via optimistic verification, batching signatures to tame size. Fireblocks and Deloitte underscore urgency; Ethereum’s quantum risk timeline compresses with each qubit milestone.
Steps to Quantum-Resistant Contracts
-

Audit existing code for vulnerabilities in pre-quantum cryptography like ECDSA or RSA, using static analysis tools to identify harvest-now-decrypt-later risks.
-

Select NIST-approved algorithms such as CRYSTALS-Dilithium (ML-DSA) for signatures and Kyber for encryption, as standardized for post-quantum security.
-
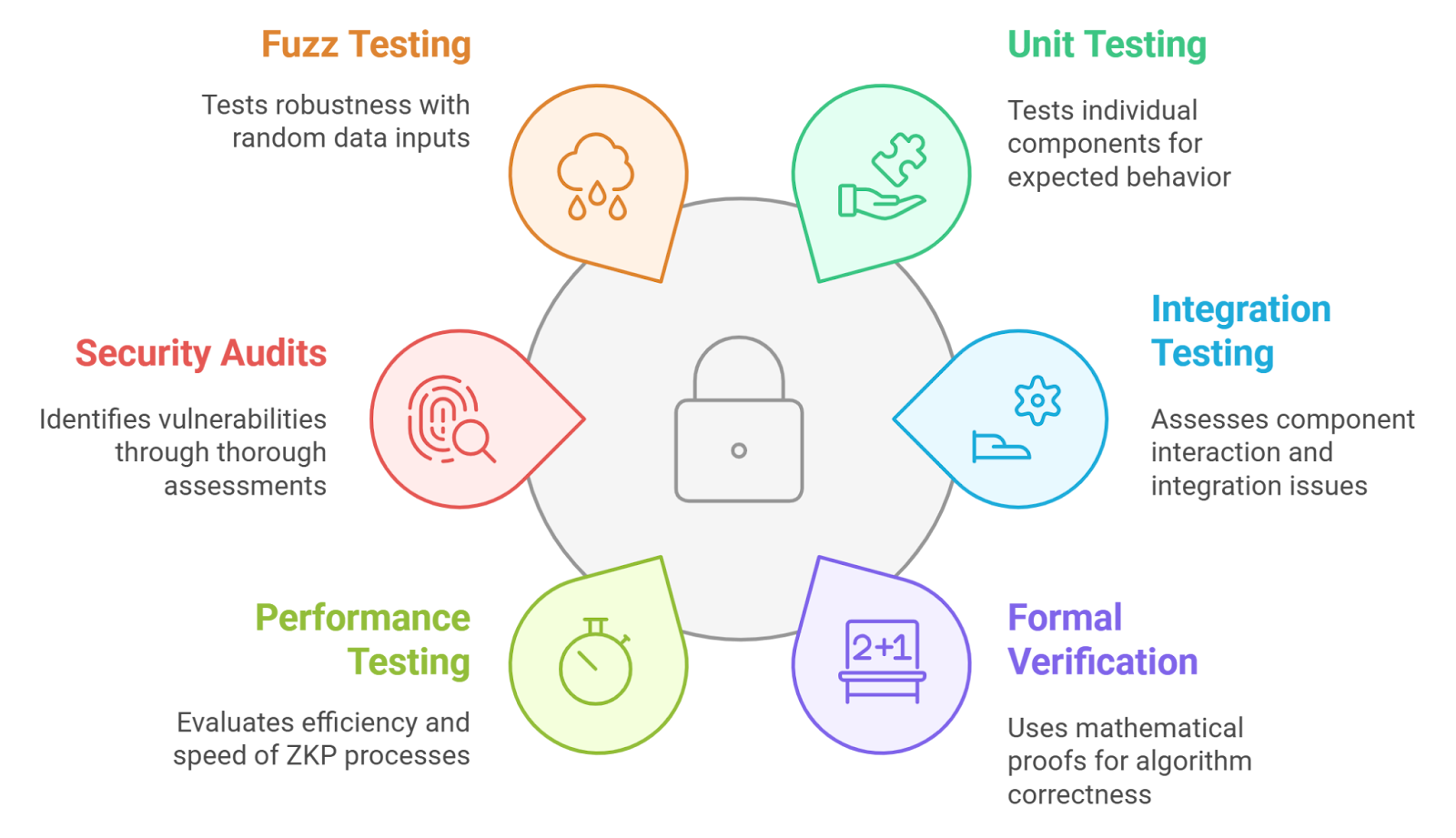
Integrate ZKPs for privacy, like zk-SNARKs in contracts such as QuantumPrivate’s PrivateVoting or zk-Agreements protocol.
-
Test on testnets like the Quantum Resistant Ledger (QRL), which uses XMSS signatures for quantum-safe validation.
-

Optimize with aggregation techniques to manage larger post-quantum signature sizes (100-1000x ECDSA), reducing blockchain bloat.
Layer-1 innovators like QRL pave the path, their XMSS ensuring unforgeable history. Rapid Innovation stresses design-from-scratch mindsets; retrofits invite exploits. LinkedIn analyses pinpoint RSA’s doom alongside ECDSA, pushing lattice dominance.
Ultimately, privacy preserving smart contracts quantum thrive on proactive diligence. As quantum shadows lengthen, platforms embedding these safeguards command premium trust. Developers and enterprises adopting now secure not just transactions, but the decentralized future itself. Encrypted smart contracts, fortified against tomorrow’s threats, unlock confidential innovation at scale.





