In the world of public blockchains like Ethereum, every piece of data stored in a smart contract lays bare for anyone to inspect. This transparency, while a boon for trustless systems, becomes a liability when handling sensitive information such as private balances, confidential bids in auctions, or user identities. Enter suint256 and saddress: encrypted types that transform Solidity into a fortress for privacy smart contracts. These Solidity encrypted types from the SeismicSystems/seismic-solidity extension let developers store and manipulate data in encrypted form, ensuring only authorized parties can decrypt it.
Traditional Solidity types like uint256 and address expose values on-chain, inviting exploits or privacy breaches. As noted in security audits, even seemingly innocuous data can leak user patterns or enable front-running. With encrypted state Solidity via Seismic’s Stypes, you declare variables that behave like their plaintext counterparts but remain ciphertexts under the hood. Computations happen securely, and storage stays confidential, bridging the gap between blockchain immutability and real-world privacy needs.
Grasping the Power of Seismic’s Encrypted Types
At its core, Seismic introduces Stypes: a suite including suint256 for unsigned integers, saddress for Ethereum addresses, and others like sbool. These aren’t mere wrappers; they’re deeply integrated with the ssolc compiler, which extends Solidity to compile encrypted logic. Picture writing familiar Solidity code, yet knowing your balances or recipient addresses hide from prying eyes. This is achieved through symmetric encryption schemes optimized for the EVM, where keys are managed off-chain or via threshold schemes for multi-party access.
I appreciate how Seismic builds on Solidity’s static typing. You specify suint256 balance; and it slots right into mappings or structs, supporting arithmetic like addition and comparisons without decryption. For saddress, transfers to encrypted recipients become possible, vital for private DeFi protocols. Security-wise, this sidesteps common pitfalls like reentrancy on visible state, as attackers see only noise. Yet, it’s reassuring: these types maintain gas efficiency close to native ones, thanks to batched operations and precompiles in fhEVM-compatible environments.
All the data recorded by a smart contract can be read by anyone. Seismic changes that equation.
Essential Setup for Secure Encrypted Development
Before diving into code, equip your toolchain. Install the Seismic Solidity extension via npm: npm install @seismicsys/seismic-solidity. This pulls in ssolc, the specialized compiler. Configure your foundry or hardhat project by overriding the solc version to ssolc in foundry. toml or hardhat. config. js. Target Solidity 0.8.34 or later, as Stypes leverage recent optimizer improvements.
Test compilation with a minimal contract. Verify deployments on testnets supporting fhEVM, like Sepolia forks with Seismic precompiles. Key best practice: always pair with view functions that decrypt only for authorized callers using signature verification, akin to EIP-712 patterns but for ciphertexts. This setup fortifies against the vulnerabilities plaguing standard contracts, from integer overflows to access control slips, as outlined in Consensys and RareSkills guides.
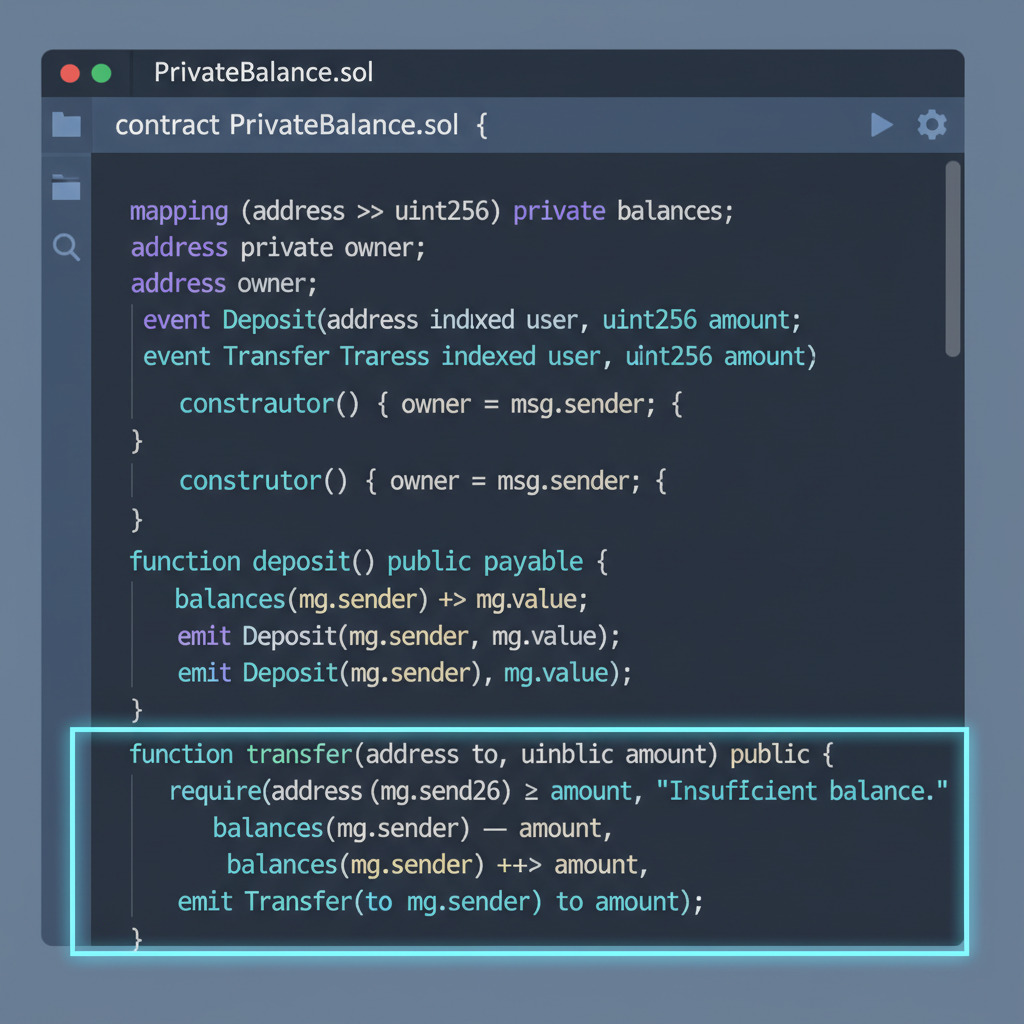
Let’s implement a private balance holder. Start with imports: Operations shine: Gas costs? Expect 2-5x native for encryption ops, but optimizations in Seismic reduce this. Audit your keys rigorously; mismanagement invites loss. In my experience auditing financial contracts, this encrypted layer adds resilience without overcomplicating logic, empowering teams to deploy confidently. Delving deeper into saddress encrypted smart contracts, these types enable recipient anonymity in transfers, a staple for privacy-focused DeFi. Assign via Seismic’s strength lies in fhEVM compatibility, letting you perform computations on ciphertexts directly in the EVM. For instance, compare balances: Branching logic demands care; use zero-knowledge proofs for complex conditions, hybridizing with Stypes. Threshold decryption adds multi-sig security, distributing keys across parties. Reassuringly, Seismic’s docs emphasize revert patterns that avoid partial decryptions, a nod to battle-tested Solidity security from ConsenSys checklists. Transitioning to production, compile with Consider a voting DAO: suint256 votesPerProposal mappings keyed by saddress voters. Tallying sums homomorphically, revealing only aggregates. This scales to enterprise, where privacy smart contracts Solidity handle HR data or IP bids without leaks. Gas benchmarks? Simple encrypted stores cost ~150k, viable for high-value txs. Challenges persist; key rotation requires careful migrations, and oracle feeds need encrypted inputs. Yet, Seismic mitigates with migration helpers. Pair with account abstraction for seamless UX, where wallets handle enc/dec off-chain. From my FRM lens, this aligns risk models: privacy reduces correlation attacks, bolstering portfolio security in DeFi. Embracing suint256 Solidity and saddress isn’t just technical; it’s a strategic pivot toward sustainable blockchain apps. Developers gain tools to match Web2 privacy without silos, fostering trust in secure contract protocols Ethereum demands. As fhEVM matures, expect widespread adoption, turning public chains into private powerhouses. Start small, audit thoroughly, and watch your contracts safeguard what matters most. Hands-On: Declaring and Using suint256 in Practice
import "@seismicsys/seismic-solidity/Stypes. sol";. Declare suint256 private userBalance;. Initialization happens via an encrypt function, say function deposit(uint256 amount, bytes32 key) public { userBalance = Stypes. encrypt(amount, key); }. Here, the caller supplies an encryption key, ensuring only they control decryption. function addBalance(suint256 delta) public { userBalance = userBalance and delta; }. Under ssolc, this compiles to homomorphic additions on ciphertexts, no plaintext exposure. For saddress, envision a confidential transfer: saddress recipient; function transfer(suint256 amt, saddress to, bytes32 key) public {/* decrypt check, then update */}. This pattern underpins secure contract protocols Ethereum devs crave for DEXes or voting systems. saddress recipient = Stypes. encryptAddress(targetAddress, key);. Validation uses homomorphic equality checks, confirming matches without revealing identities. This shines in blind auctions, where bids pair encrypted amounts with saddress bidders, preventing collusion. Advanced Operations and fhEVM Integration
if (userBalance and gt; threshold) {/* conditional logic */}. ssolc translates this to FHE operations via precompiles, preserving encrypted state Solidity. I’ve seen teams build confidential lending protocols this way, where interest accrues privately until repayment. Opinion: while gas premiums exist, they’re a small price for shielding strategies from MEV bots, far outweighing the risks of public state. Real-World Deployment: From Code to Confidential Chains
ssolc --optimize contract. sol -o build/, then deploy via Forge scripts adapted for Seismic. Target chains with fhEVM flags, like upcoming Ethereum L2s or Sepolia proxies. Verification scripts decrypt views post-deployment, confirming integrity. In audits, I stress fuzzing encrypted inputs; tools like Echidna now support Stypes mocks, catching overflows in ciphertext arithmetic.