Programmable privacy is quietly transforming how we think about encrypted smart contracts, pushing the boundaries of what’s possible in blockchain privacy protocols. Instead of choosing between transparency and confidentiality, developers can now code privacy directly into contract logic, unlocking custom data protection and selective disclosure for users and enterprises alike.
The Rise of Programmable Privacy: From Obscurity to On-Chain Innovation
Traditional blockchains made everything public by default. This openness fueled trust, but it also exposed sensitive data that businesses and individuals would rather keep private. Enter programmable privacy: a new paradigm where smart contracts can process encrypted information without ever decrypting it on-chain. This leap is powered by cryptographic breakthroughs like Fully Homomorphic Encryption (FHE) and Zero-Knowledge Proofs (ZKPs).
FHE allows computations on encrypted data as if it were plaintext, keeping all inputs, states, and outputs confidential throughout execution. Zama’s fhEVM, for example, lets Solidity developers build confidential contracts on Ethereum without needing to become cryptography experts themselves. Meanwhile, ZKPs let one party prove knowledge or correctness without revealing underlying details, enabling compliance checks or transaction validation while safeguarding user data.
This dual approach means developers can set granular rules for who sees what, and when, directly inside the contract code. The result? A new era for privacy-preserving smart contracts that doesn’t sacrifice composability or decentralization.
Platforms Leading the Programmable Privacy Movement
The ecosystem is moving fast, with several projects at the cutting edge:
- Zama Confidential Blockchain Protocol: FHE-based confidential contracts deployable on any L1 or L2, ensuring end-to-end encryption for all transactions and computations.
- Secret Network: Uses Trusted Execution Environments (TEEs) to keep contract state and logic private while allowing selective outputs as needed.
- Chainlink Confidential Compute: Blends TEEs with advanced cryptography to bring decentralized confidential computing across blockchains, ideal for institutions demanding both scalability and airtight privacy.
This wave of innovation is not just theoretical; it’s already reshaping how enterprises approach on-chain compliance and private DeFi markets. For a deep dive on programmable confidentiality in regulated environments, see this resource.
Bespoke Privacy Rules: Customizing Confidentiality On-Chain
The real power of programmable privacy lies in its flexibility. Developers can define exactly which data points are encrypted, who gets access under what conditions, and even how compliance checks are performed, all within the smart contract itself. For instance:
- A DeFi protocol might allow auditors to verify solvency via ZKPs without exposing user balances.
- An enterprise supply chain contract could share shipment status publicly but keep pricing terms confidential unless certain criteria are met.
- A healthcare dApp could process patient records securely while letting authorized providers access only relevant fragments as needed.
This programmability unlocks new business models that were previously impossible due to privacy constraints or regulatory risk. It also streamlines user experience: instead of relying on off-chain agreements or trust assumptions, everything is enforced directly by code.
As these capabilities mature, programmable privacy is set to redefine what “trustless” means in the blockchain era. We’re moving from static, one-size-fits-all privacy to dynamic, context-aware confidentiality. Smart contracts can now adapt to jurisdictional requirements, user roles, or even real-time risk signals, enabling compliance without compromising on decentralization or user sovereignty.
Key Use Cases for Programmable Privacy
-
Private DeFi Lending & Trading (Secret Network): Secret Network enables encrypted smart contracts for DeFi apps, allowing users to trade, lend, and borrow assets without exposing sensitive transaction data or portfolio details to the public blockchain.
-

Confidential Supply Chain Agreements (Zama Confidential Blockchain Protocol): Zama’s Confidential Blockchain Protocol uses Fully Homomorphic Encryption (FHE) to let companies execute supply chain smart contracts that keep proprietary pricing, supplier identities, and logistics data confidential while maintaining verifiable compliance.
-
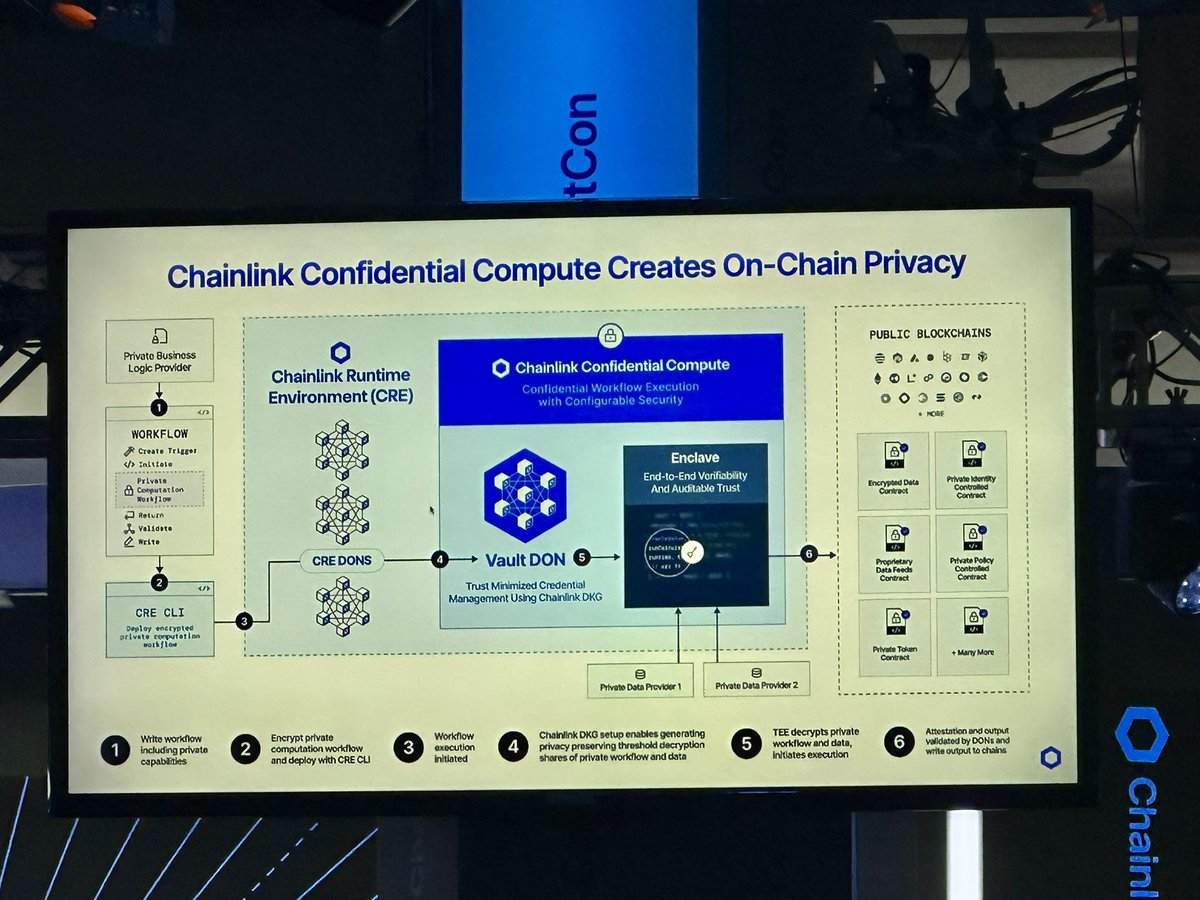
Privacy-Preserving Healthcare Data Sharing (Chainlink Confidential Compute): Chainlink Confidential Compute combines Trusted Execution Environments (TEEs) and cryptography to process patient records and medical research data securely on-chain, ensuring data privacy and regulatory compliance for healthcare providers and researchers.
-
On-Chain Identity Verification with Zero-Knowledge Proofs (zkSync): zkSync leverages Zero-Knowledge Proofs (ZKPs) for private, on-chain digital identity verification, allowing users to prove eligibility or credentials without revealing personal information.
-

Private Institutional Settlements (Polygon zkEVM): Polygon zkEVM utilizes ZKPs to enable private, compliant settlement of large institutional trades on-chain, protecting trade details from public view while ensuring regulatory requirements are met.
This evolution isn’t happening in a vacuum. Regulatory frameworks are quickly catching up, with programmable privacy offering a toolkit for meeting global data protection laws while keeping core operations on-chain. Enterprises can automate selective disclosure, think KYC checks or audit trails, without leaking sensitive commercial information. For more on navigating compliance with encrypted smart contracts, visit our compliance guide.
Challenges and Next Frontiers: Scaling Privacy for the Real World
Despite the promise, several challenges remain. FHE and ZKP-based protocols are computationally intensive; optimizing for speed and cost is an active area of research. Interoperability between privacy-preserving platforms and legacy blockchains is still maturing. User experience also needs refinement, abstracting away cryptographic complexity so developers and end-users interact seamlessly with encrypted smart contracts.
Yet the momentum is undeniable. As more toolkits emerge (like Zama’s fhEVM or Secret Network’s TEE stack), we’ll see wider adoption across both public blockchains and enterprise consortia. Privacy will no longer be an afterthought but a programmable feature as integral as consensus or composability.
Ultimately, programmable privacy unlocks a spectrum of possibilities, from confidential DeFi trading to private digital identity, and empowers developers to build trustless systems that respect user autonomy at every layer. This shift isn’t just technical; it’s philosophical. The future of blockchain will be both transparent and private, by design.






