Smart contracts have become the backbone of decentralized applications, automating agreements and transactions with unprecedented transparency. Yet, this very transparency has long been a double-edged sword: while it fosters trust in open networks, it also exposes sensitive data to every participant on the blockchain. For industries and users demanding confidentiality, this creates a significant barrier to adoption. Enter Fully Homomorphic Encryption (FHE), a cryptographic breakthrough that is quickly emerging as the keystone for truly usable privacy in smart contracts.
What Makes FHE a Privacy Game-Changer?
At its core, FHE enables computations to be performed directly on encrypted data. This means that even as smart contracts execute complex logic, neither the nodes running them nor any external observer can access the raw input, state, or output values. Only authorized parties with the appropriate decryption keys can ever reveal the underlying information. This is a radical departure from traditional blockchains, where all data processed by smart contracts is visible by default.
The implications are profound. With FHE-powered smart contracts:
- User data remains confidential throughout its lifecycle – at rest, in transit, and during computation.
- Developers can build dApps for sensitive sectors like finance, healthcare, and supply chain without exposing proprietary or personal information to competitors or the public.
- Regulatory compliance becomes more attainable, as encrypted processing aligns with privacy-by-design mandates found in GDPR and similar frameworks.
This technological leap is not just theoretical. Multiple projects are already demonstrating real-world viability by integrating FHE into blockchain protocols and virtual machines. For an in-depth look at how these integrations work on Ethereum-compatible chains, see our technical guide here.
The Mechanics: How FHE Secures Smart Contract Computation
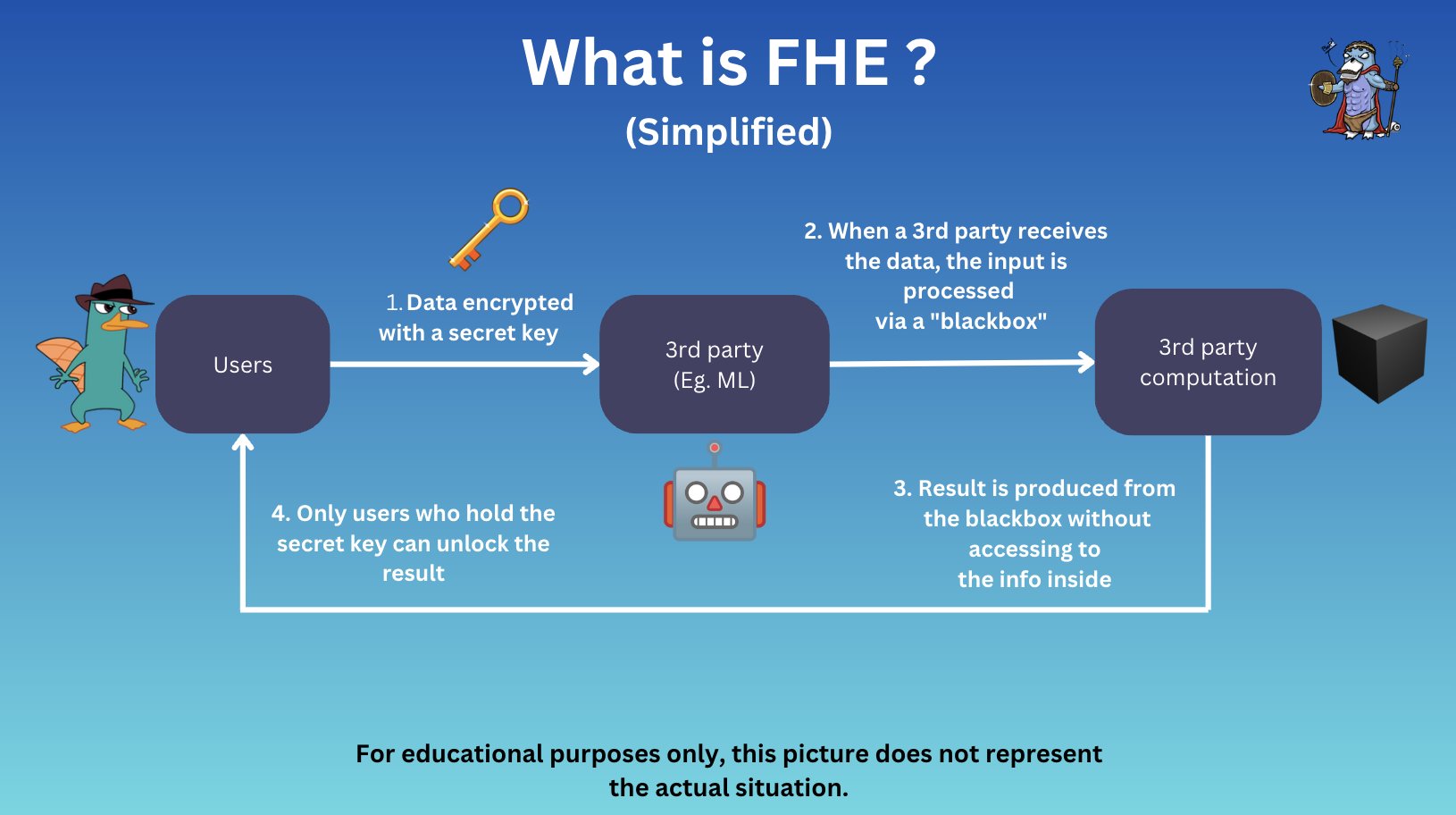
To appreciate why FHE is so powerful for privacy-preserving blockchain protocols, it’s helpful to understand its basic mechanics. Conventional encryption schemes allow either secure storage (data at rest) or secure transmission (data in transit), but require decryption before computation, creating a privacy gap during processing. FHE closes this gap entirely.
An FHE scheme consists of three main algorithms:
- KeyGen: Generates public/private keys and parameters for encryption and decryption.
- Encrypt/Decrypt: Securely encrypts plaintext into ciphertext and recovers plaintext from ciphertext using secret keys.
- Evaluate: Allows arbitrary computations directly on ciphertexts, producing an encrypted result that matches what would be obtained if computed on plaintext.
This means miners or validators can execute contract logic over encrypted inputs without ever seeing the underlying data. When the result is decrypted by an authorized party, it matches exactly what would have been produced had all operations occurred in plain sight, but no one except the keyholder ever sees anything unencrypted.
Pioneering Implementations: From Theory to Practice
The past year has seen rapid progress in making FHE practical for blockchain environments, traditionally notorious for their computational constraints. Notable developments include:
- Zama’s fhEVM: A groundbreaking extension of Ethereum’s virtual machine enabling developers to write Solidity contracts that process encrypted inputs natively. This allows privacy-preserving dApps without requiring deep cryptographic expertise (learn more about fhEVM architecture here).
- smartFHE Framework: An architecture where miners perform computations over ciphertexts while users prove their private inputs’ validity using efficient zero-knowledge proofs, minimizing user-side computational burden.
This shift from theory to practice signals a new era where confidential computation is not only possible but increasingly usable within mainstream blockchain ecosystems.
Despite the promise, integrating Fully Homomorphic Encryption into smart contracts is not without its hurdles. The computational demands of FHE are still orders of magnitude higher than traditional cryptography, leading to latency and throughput challenges. However, advances in algorithmic efficiency and hardware acceleration are rapidly narrowing this gap. Projects like Zama’s fhEVM are already demonstrating that privacy-preserving dApps can achieve practical performance for many real-world applications.
Another key consideration is usability for developers and end-users. Historically, leveraging advanced cryptography has required deep domain expertise, but modern frameworks are abstracting away much of this complexity. For example, fhEVM lets Solidity developers write encrypted smart contracts with minimal changes to their existing workflows. The smartFHE framework further reduces friction by offloading heavy computations to miners and relying on zero-knowledge proofs for efficient input validation.
Unlocking New Use Cases With Confidential Computation
The ability to process encrypted data unlocks a wave of new decentralized applications that were previously infeasible on public blockchains:
Novel Use Cases Enabled by FHE-Powered Smart Contracts
-
Private DeFi Lending and Borrowing: FHE-powered smart contracts enable confidential lending and borrowing on platforms like Zama’s fhEVM, where users’ collateral amounts, loan terms, and interest rates remain encrypted, protecting sensitive financial details from public view while maintaining trustless execution.
-

Privacy-Preserving Healthcare Data Sharing: With frameworks such as smartFHE, healthcare providers can deploy smart contracts that process encrypted patient data for research or insurance claims, ensuring that personal health information remains confidential throughout computation and storage on the blockchain.
-

Confidential Blockchain Voting Systems: FHE enables the creation of smart contracts for secure and private voting, where individual ballots are encrypted and tallied without exposing voters’ choices, supporting transparent yet confidential elections on blockchain platforms.
-
Secure Supply Chain Auditing: By leveraging FHE, supply chain participants can share encrypted data about product origins, certifications, and compliance records. Smart contracts can verify and audit these records without revealing proprietary or sensitive business information to competitors or the public.
Decentralized finance (DeFi) protocols can now offer private lending, confidential asset management, or blind auctions without exposing user positions or strategies. In healthcare, patient records could be managed by smart contracts that enforce access controls and compliance policies while never revealing sensitive details on-chain. Voting systems can guarantee ballot secrecy without sacrificing auditability or trustlessness. Even in supply chain management, proprietary business data can remain protected while still benefiting from blockchain’s transparency and automation.
This paradigm shift is not limited to theory or pilot projects; it is being actively explored across the industry as regulatory scrutiny over data privacy intensifies. As more platforms adopt encrypted smart contract architectures, we will see a proliferation of privacy-preserving blockchain protocols tailored to both enterprise and consumer needs.
The Road Ahead: Usable Privacy at Scale
The next phase for FHE in blockchain will focus on scalability and interoperability. Researchers are working on batching techniques and hybrid models that combine FHE with other cryptographic primitives like secure multi-party computation (MPC) or trusted execution environments (TEEs) to optimize cost-performance tradeoffs. Standardization efforts are also underway to ensure cross-chain compatibility for encrypted contract protocols.
The ultimate vision is a world where users no longer have to choose between decentralization and confidentiality, where privacy is a default feature rather than an afterthought.
If you’re interested in technical deep dives or hands-on guides for building with FHE-based confidential smart contracts on Ethereum-compatible chains, check out our comprehensive resource here.
The maturation of fully homomorphic encryption marks a pivotal turning point for blockchain usability and adoption. By making strong privacy compatible with open networks and programmable money, FHE isn’t just an incremental upgrade, it’s the foundation for the next generation of secure digital agreements.






