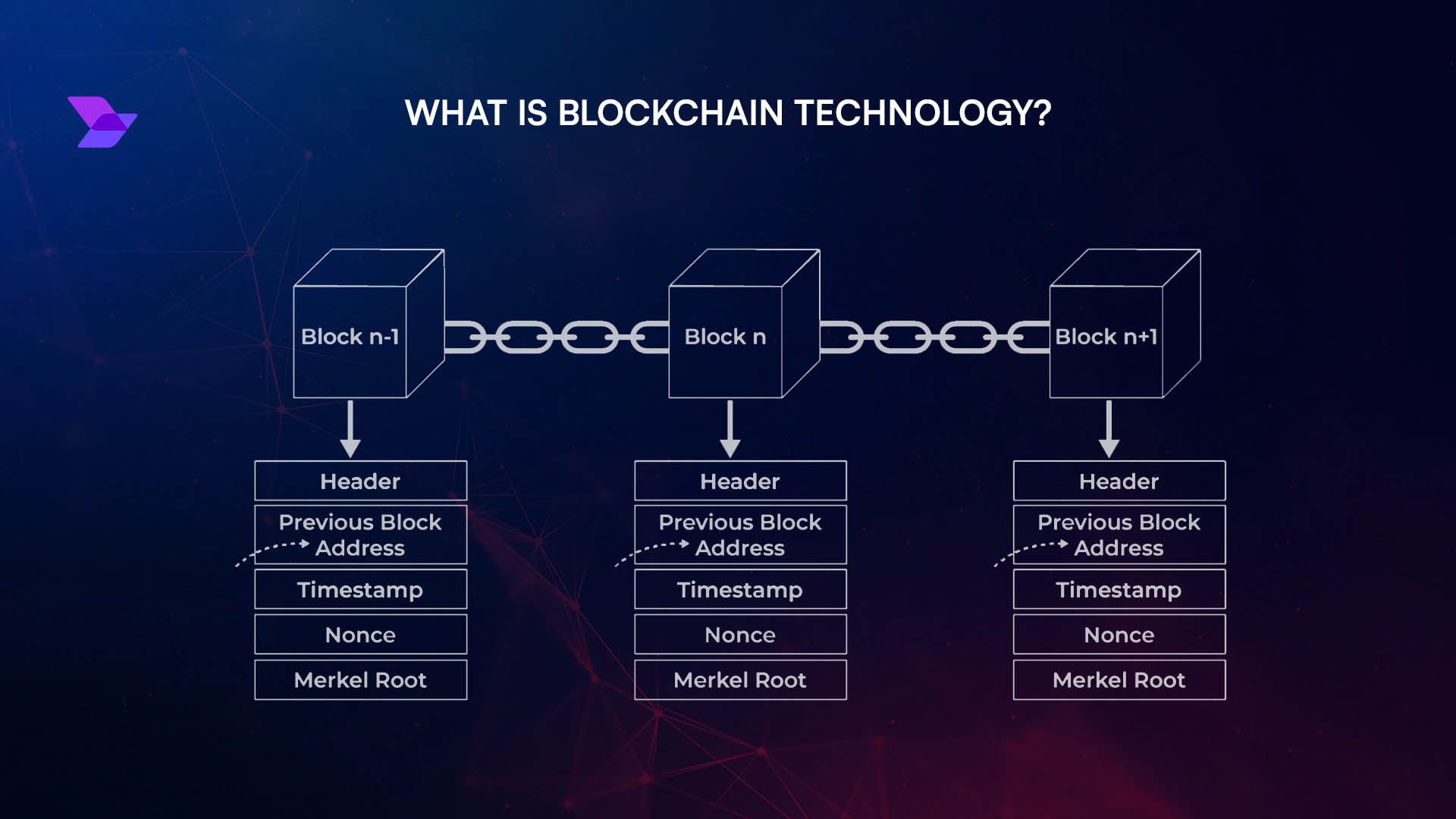
Confidentiality is the new frontier for business transactions on Ethereum. As enterprises increasingly turn to blockchain for automation, transparency, and efficiency, the need to protect sensitive business logic and data becomes paramount. Standard smart contracts broadcast every transaction and variable state to the public ledger – a dealbreaker for businesses handling proprietary information or regulated data. Enter encrypted smart contracts, which enable confidential agreements, private financial flows, and secure multiparty computation directly on-chain.
Why Confidentiality Matters in Business Smart Contracts
Traditional Ethereum contracts are transparent by design. While this suits open DeFi protocols, it’s a non-starter for use cases like payroll, supply chain deals, or healthcare records where exposure of contract terms or participant identities could be catastrophic. Confidential smart contract implementation unlocks blockchain’s automation while keeping critical data shielded from competitors, regulators, or even curious network participants.
- Competitive Advantage: Keep contract logic and terms private from rivals.
- Regulatory Compliance: Protect personal data under GDPR or HIPAA mandates.
- Secure Negotiations: Enable trustless yet private bidding and settlement.
The Core Methods: How Encrypted Smart Contracts Work on Ethereum
The past year has seen rapid innovation in blockchain privacy solutions. Today’s developers can choose from several robust approaches to achieving Ethereum confidential transactions, each with its own tradeoffs in security, scalability, and developer experience:
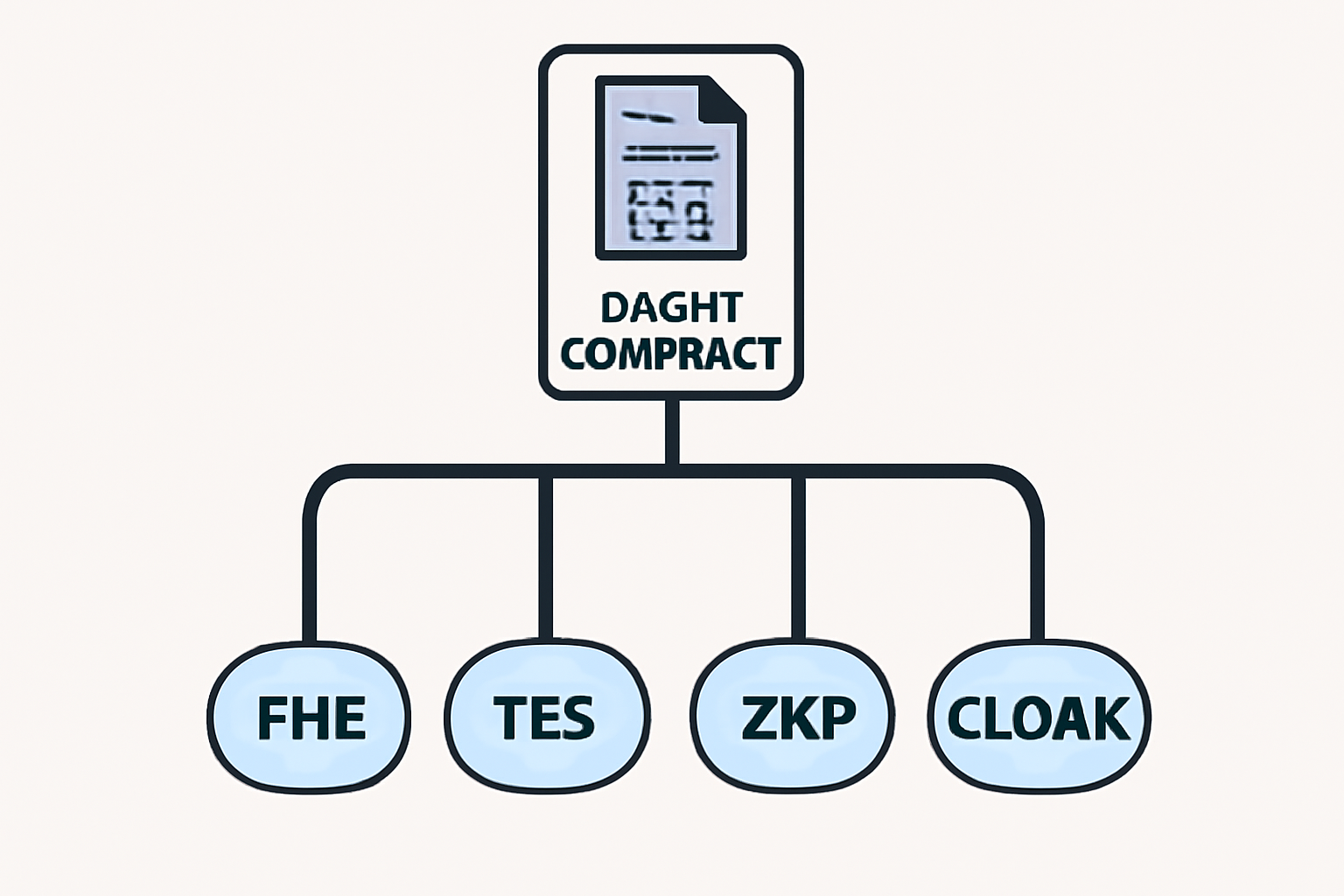
Core Methods for Encrypted Smart Contracts
-
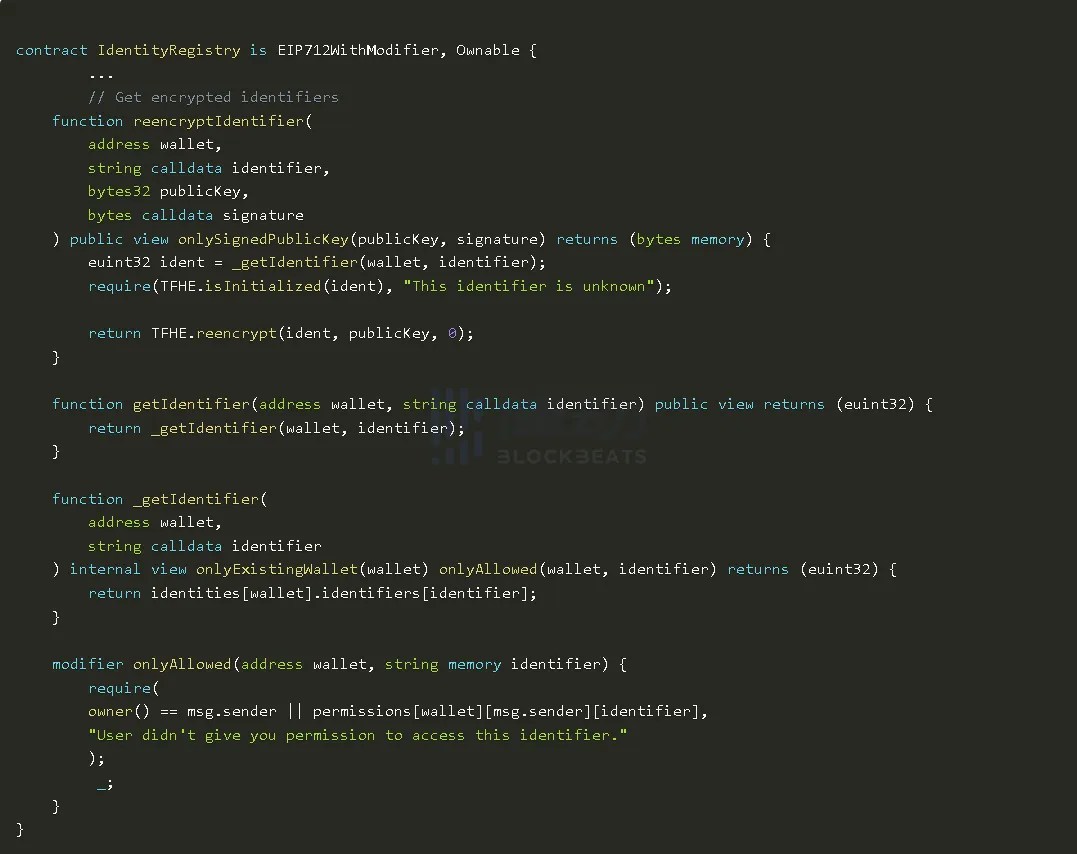
Fully Homomorphic Encryption (FHE) via Zama’s fhEVM: FHE enables computations on encrypted data without decryption. Zama’s fhEVM lets developers write confidential smart contracts in Solidity using euint types, keeping sensitive data private on-chain.
-
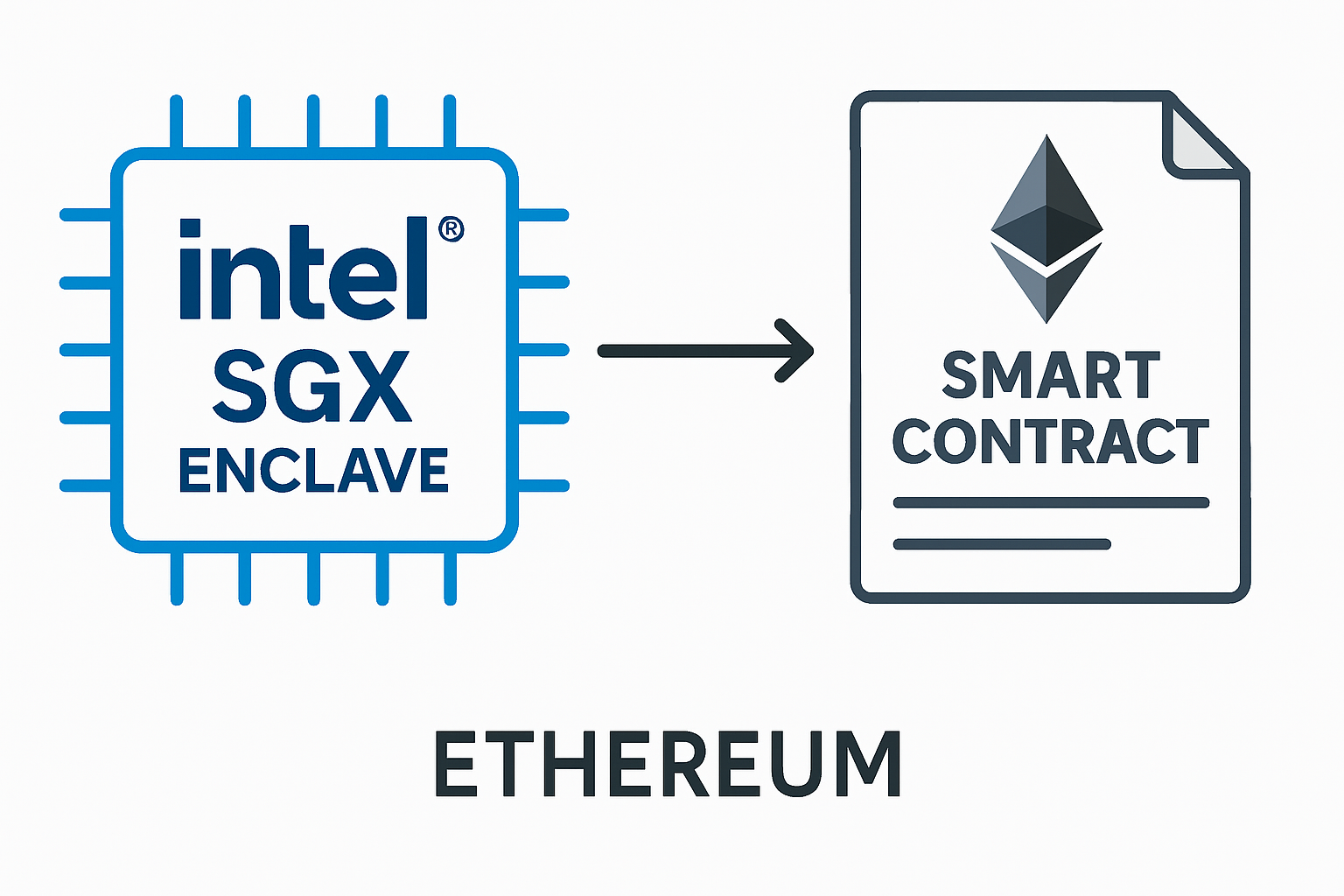
Trusted Execution Environments (TEE) such as Intel SGX: TEEs provide isolated hardware environments to securely execute contract logic. Deploying smart contracts within Intel SGX enclaves ensures data and code confidentiality, with encrypted inputs/outputs and attestation for verification.
-

Zero-Knowledge Proofs (ZKPs) with the Zether Protocol: ZKPs allow validation of transactions without revealing underlying data. The Zether protocol integrates with Ethereum to keep account balances and transactions confidential using cryptographic proofs.
-

Confidential Token Standards: zkERC20: The zkERC20 standard brings confidential transactions to Ethereum tokens, using zero-knowledge proofs to hide transfer amounts while ensuring transaction validity and network security.
-
Privacy Frameworks like CLOAK: CLOAK is a framework for developing and deploying confidential smart contracts with multi-party transactions. It automates privacy policy enforcement and runtime generation, simplifying confidential contract creation.
Fully Homomorphic Encryption (FHE):
This cryptographic breakthrough allows computations directly on encrypted data, no decryption required at any step. Zama’s fhEVM lets Solidity devs use special encrypted types (like euint) for confidential logic. All sensitive variables remain opaque even as the contract runs. For technical details and code samples see the Zama documentation.
Trusted Execution Environments (TEE):
This hardware-based approach leverages secure enclaves (such as Intel SGX) to process contract logic in isolation from the rest of the system. Inputs are encrypted outside the enclave; only attested outputs hit the blockchain. Explore implementation strategies in this peer-reviewed study: MDPI – Confidential Smart Contracts Using TEEs.
Zero-Knowledge Proofs (ZKPs):
ZKPs let you prove you know something, like a password or transaction value, without revealing what it is. The Zether protocol overlays ZKP-based confidentiality atop Ethereum accounts for private transfers and balances (read more here). Similarly, zkERC20 introduces stealthy token transfers using zero-knowledge proofs (zkERC20 standard).
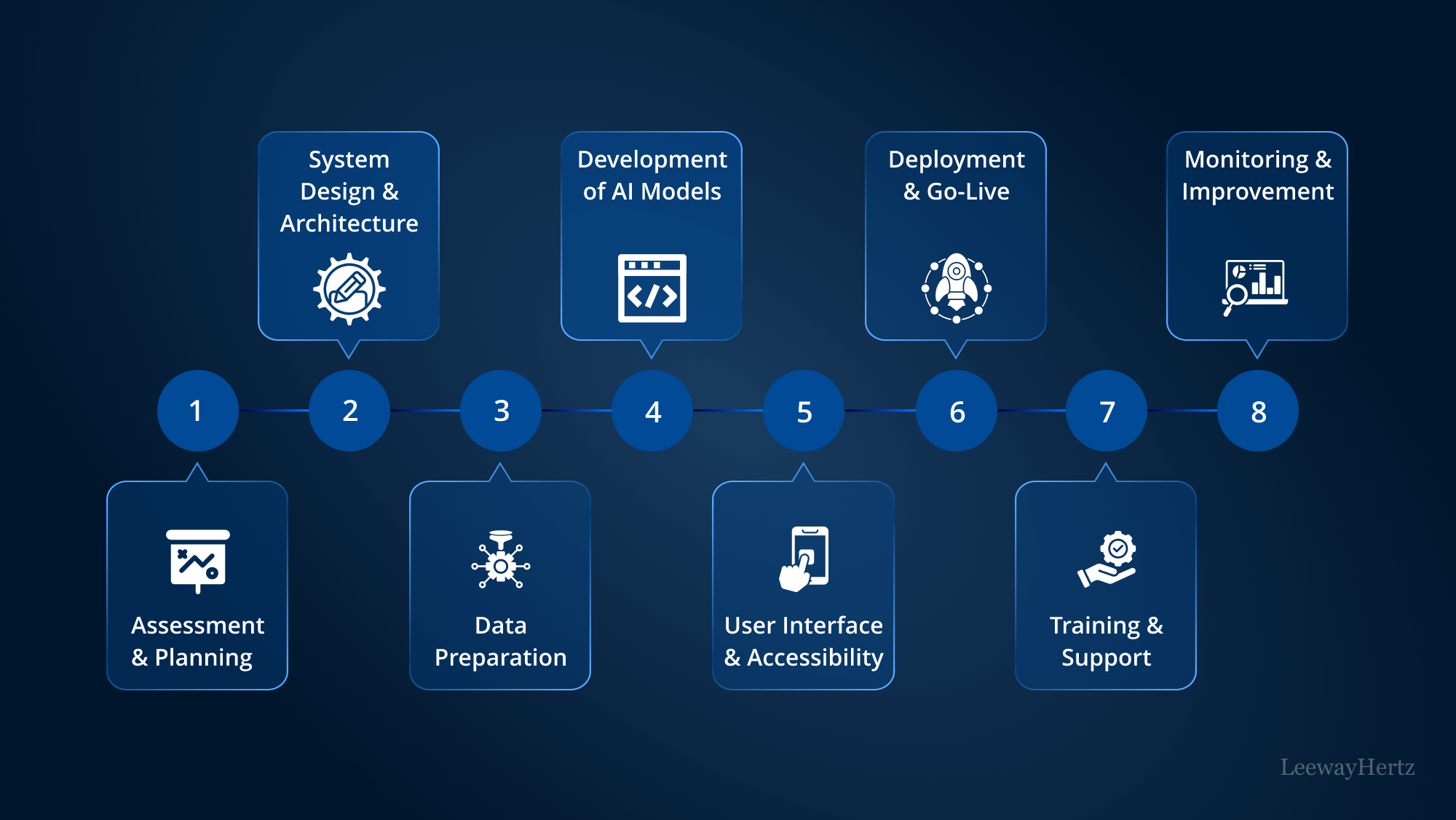
A Practical Roadmap: From Concept to Confidential Contract Deployment
Pioneering privacy smart contract implementation starts with clear business goals, then moves into technical execution using modern frameworks:
- Define What Needs To Be Private: Is it transaction amounts? Participant identities? Contract state?
- Select Your Privacy Tech Stack: FHE for all-on-chain encryption; TEE if you prefer hardware-backed security; ZKPs for advanced proofs-without-revelation.
- Coding and Testing: Use specialized libraries (e. g. , fhEVM) and testnets designed for privacy features before mainnet deployment.
- Sustained Monitoring: Once live, monitor your contracts not just for bugs but also potential side-channel leaks or performance bottlenecks unique to encrypted execution.
The Business Impact of Secure Blockchain Automation
The ability to create secure business contracts on blockchain without sacrificing confidentiality marks a paradigm shift for enterprise adoption. With privacy frameworks like CLOAK simplifying multi-party confidential workflows (see CLOAK framework details here) and token standards like zkERC20 ensuring stealthy value transfer, organizations can finally automate, and scale, complex agreements without exposing their crown jewels.
Privacy is no longer a luxury, it’s a baseline expectation for any meaningful enterprise blockchain deployment. As confidential smart contract technologies mature, we’re seeing a new breed of business automation: one where sensitive negotiations, settlements, and compliance processes happen entirely on-chain, yet remain invisible to the public. This unlocks a host of new use cases, from private auctions and sealed-bid tenders to confidential payroll and supply chain finance, all powered by Ethereum’s security and composability.
Key takeaway: Encrypted smart contracts don’t just hide data, they enable new business logic that was previously impossible on transparent ledgers.
Challenges and Best Practices for Privacy Smart Contract Implementation
While the cryptographic building blocks are powerful, implementing privacy smart contracts is not plug-and-play. Developers and business leaders should be aware of practical challenges:
- Performance Overhead: Methods like FHE and ZKPs can increase gas costs and latency. Benchmark carefully and optimize contract logic for privacy-specific bottlenecks.
- Complexity: Confidential contracts require a deeper understanding of cryptography and threat modeling. Leverage open-source frameworks and peer-reviewed standards to avoid custom vulnerabilities.
- Interoperability: Not all privacy solutions are natively compatible with existing DeFi protocols or wallets. Plan for integrations and educate users on private transaction flows.
- Regulatory Considerations: Enhanced privacy can complicate auditability and compliance. Build in selective disclosure features where mandated.
Top Open-Source Tools for Encrypted Ethereum Smart Contracts
-

Zama fhEVM: An open-source EVM extension enabling fully homomorphic encryption (FHE) in Solidity smart contracts. Developers can use euint types for confidential computations directly on Ethereum. Learn more.
-
CLOAK Framework: A privacy-focused framework for developing and deploying confidential smart contracts with multi-party transactions. It automates privacy enforcement and runtime generation. See details.
-
Zether Protocol: An open-source protocol using zero-knowledge proofs (ZKPs) for confidential Ethereum transactions. Developed by Stanford and Visa Research, it encrypts balances and transaction details. Read more.
-

zkERC20 Standard: An open-source confidential token standard for Ethereum, leveraging ZKPs to hide transaction amounts while maintaining security and compliance. Explore zkERC20.
-
Open Enclave SDK: An open-source SDK for building Trusted Execution Environment (TEE)-based smart contracts, supporting confidential execution with hardware-backed security (e.g., Intel SGX). Discover Open Enclave SDK.
For teams ready to take the plunge, start with pilot deployments on testnets or private chains. Use robust monitoring to detect unusual patterns and validate that no sensitive data leaks through side channels or event logs. And always keep an eye on the evolving landscape, privacy tech is moving fast, and today’s best practices may be tomorrow’s legacy.
Real-World Scenarios: Confidential Business Transactions in Action
Let’s make this tangible. Imagine a pharmaceutical supply chain using encrypted smart contracts to automate order fulfillment. Each shipment’s details, pricing, and participant identities remain confidential, while the blockchain still guarantees authenticity and settlement. Or consider a cross-border payroll system where employee salaries are processed privately via zkERC20 tokens, no more leaking sensitive compensation data to the public ledger.
These aren’t hypotheticals, they’re live pilots and prototypes made possible by the latest privacy frameworks. As adoption grows, expect to see confidential business logic become a default expectation in sectors where data sensitivity is paramount.
Next Steps: Building Your First Encrypted Smart Contract
Ready to experiment? Here’s a quick checklist to guide your journey:
The future of secure business contracts on blockchain is visual, composable, and private by design. With encrypted smart contracts, Ethereum finally delivers on the promise of programmable money for enterprises that demand confidentiality as much as trustlessness.