
Privacy is the new power play in DeFi. As the sector explodes with innovation, developers and enterprises are demanding blockchain privacy solutions that deliver bulletproof confidentiality without sacrificing usability or composability. The latest breakthroughs in encrypted smart contracts are making confidential DeFi transactions not just possible, but practical and scalable. If you’ve been waiting for a sign to dive into secure DeFi development, this is it.
Why Confidentiality Is Non-Negotiable in DeFi
Traditional blockchains broadcast every transaction detail to the world – great for transparency, disastrous for privacy. In the cutthroat world of decentralized finance, exposing your trading strategies, liquidity positions, or loan data can spell disaster. That’s why privacy smart contracts have become the holy grail for serious DeFi builders.
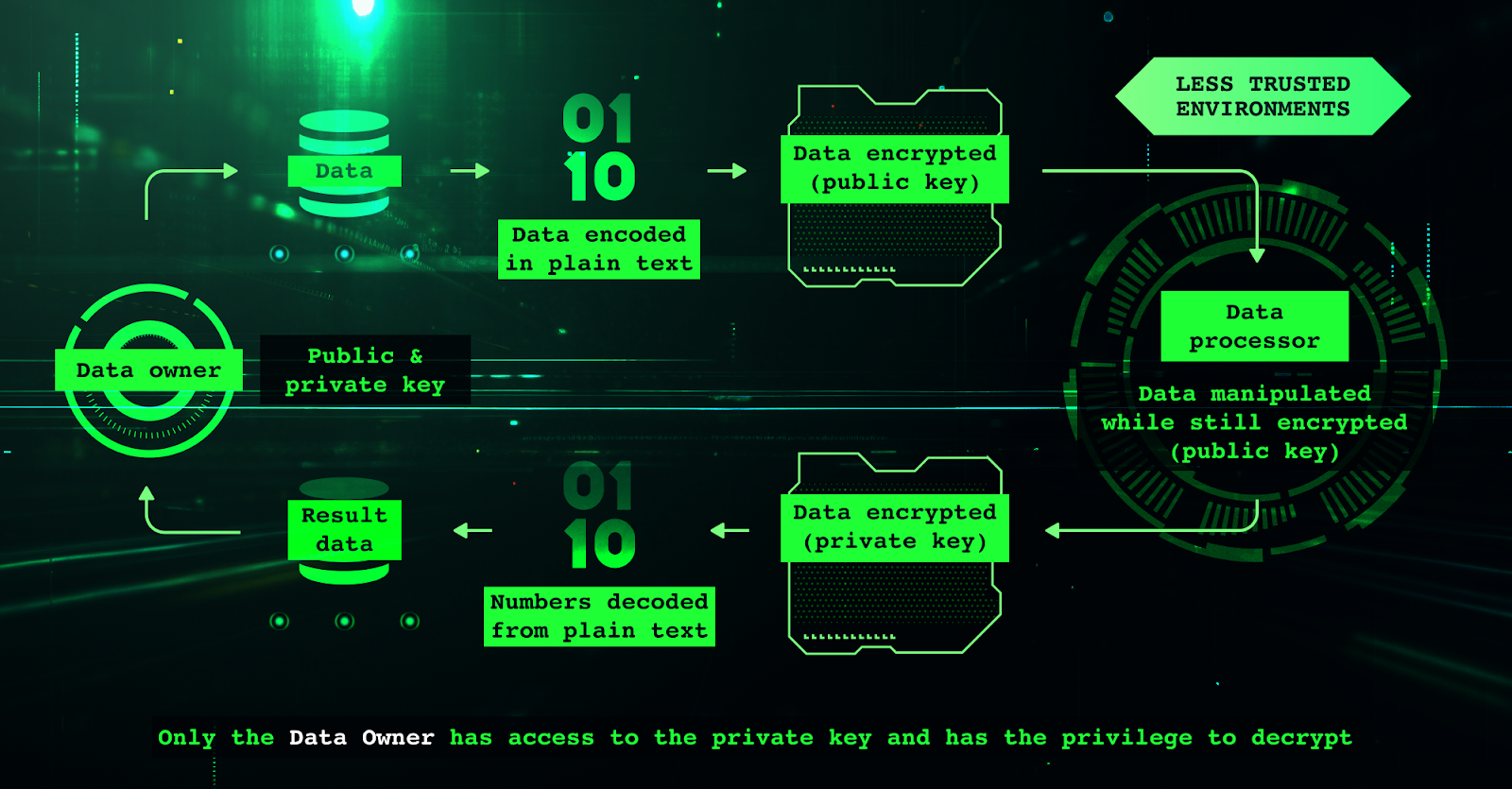
The market has responded with a surge of innovation. Zama’s Fully Homomorphic Encryption Virtual Machine (fhEVM) now lets you write encrypted smart contracts directly in Solidity. This means end-to-end encryption of transaction data and on-chain states – even during processing. No more trade-offs between privacy and programmability.
The Tech Stack: How Encrypted Smart Contracts Work
The magic behind confidential DeFi transactions lies in integrating advanced cryptography directly into your smart contract workflow. Here are the core components powering today’s leading blockchain privacy solutions:
Key Technologies Powering Confidential Smart Contracts
-

Zama’s Fully Homomorphic Encryption Virtual Machine (fhEVM): Enables developers to write confidential smart contracts in Solidity, allowing encrypted data processing on-chain without decryption. This breakthrough makes end-to-end encrypted DeFi applications possible.
-

Confidential Token Standard by Zama & OpenZeppelin: A new Confidential Token interface—similar to ERC20 but with encrypted balances and transactions—sets open-source standards for privacy-first DeFi and digital assets.
-

Secret Network Confidential Computing Layer: Provides a Confidential Computing Layer compatible with EVM, Cosmos SDK, and Solana, empowering dApps to utilize encrypted data for use cases like private voting and secure randomness.
-

Secure Oracles with Confidential Computing: Confidential computing technologies, such as Trusted Execution Environments (TEEs), secure blockchain oracles and smart contract execution, protecting sensitive off-chain and on-chain data feeds.
-

Developer Resources from Zama: Zama offers video tutorials and guides for implementing confidential smart contracts with fhEVM, giving developers practical tools to enhance DeFi privacy.
Fully Homomorphic Encryption (FHE): This is the game-changer. FHE allows computations on encrypted data without ever decrypting it – meaning sensitive information stays secret throughout execution. Zama’s fhEVM is setting the pace here by making FHE accessible to Solidity developers (see Zama’s tutorial).
Confidential Token Standards: In July 2025, Zama and OpenZeppelin introduced a production-ready confidential token interface similar to ERC20 but with encrypted balances and transaction values. This is a giant leap toward making privacy the default in DeFi (read about their partnership here).
Confidential Computing Layers: Networks like Secret Network offer EVM-compatible layers that enable decentralized apps to leverage encrypted data for everything from private voting to secure random number generation (learn more about Secret Network’s Confidential Computing Layer).
Your First Steps: Setting Up for Secure DeFi Development
If you’re ready to build your first encrypted smart contract for confidential DeFi transactions, start by upgrading your toolset:
- Solidity and fhEVM: Download and integrate Zama’s fhEVM coprocessor into your development stack.
- Migrate to Confidential Token Standards: Study OpenZeppelin’s implementation and adapt it for your own use cases.
- Dive Into Tutorials: Take advantage of step-by-step guides from pioneers like Zama (watch their video walkthrough here).
- Tinker with Secure Oracles and Off-Chain Components: Explore how confidential computing can secure your app’s external data feeds.
The learning curve is real – but so are the rewards. With these tools and frameworks at your fingertips, you’re poised to create next-generation privacy smart contracts that empower users without compromise.
Once you’ve got your development stack ready, it’s time to focus on the practical challenges and best practices that will set your confidential DeFi project apart. The difference between a good implementation and an exceptional one comes down to understanding the nuances of encrypted smart contracts, especially when integrating with existing DeFi protocols and user interfaces.
Best Practices for Building Privacy-First Smart Contracts
Developers are no longer flying blind, there’s a clear path to building robust privacy smart contracts. Here’s what separates high-impact DeFi projects from the rest:
Best Practices for Encrypted Smart Contracts in DeFi
-
Leverage Zama’s fhEVM for End-to-End Encryption: Utilize Zama’s Fully Homomorphic Encryption Virtual Machine (fhEVM) to write confidential smart contracts in Solidity, ensuring transaction data and on-chain states remain encrypted throughout processing.
-

Adopt the Confidential Token Standard by Zama & OpenZeppelin: Implement the new Confidential Token standard, which encrypts balances and transaction values, to make privacy the default for DeFi assets. This standard is backed by the Confidential Token Association.
-
Integrate Secure Oracles and Confidential Computing Layers: Use solutions like Secret Network’s Confidential Computing Layer to securely process encrypted data for use cases such as private voting and secure randomness.
-

Follow Open-Source Standards and Audit Best Practices: Align with open-source standards from the Confidential Token Association and utilize trusted auditing frameworks like OpenZeppelin to ensure your encrypted smart contracts are robust and secure.
-

Stay Updated with Developer Tutorials and Community Resources: Regularly consult resources such as Zama’s video tutorials and community forums to keep up with the latest best practices and technical advancements in confidential smart contract development.
1. Prioritize User Experience: Encrypted transactions can introduce friction if not handled thoughtfully. Use intuitive wallet integrations and clear transaction feedback so users always know their data is protected, without sacrificing speed or usability.
2. Optimize Gas Efficiency: FHE computations are powerful but computationally intensive. Profile your contract logic for bottlenecks, leverage batching where possible, and tap into community-driven optimizations to keep fees competitive.
3. Embrace Open Standards: Don’t reinvent the wheel, build on open-source confidential token standards like those from Zama and OpenZeppelin. This ensures interoperability and long-term support as privacy infrastructure matures.
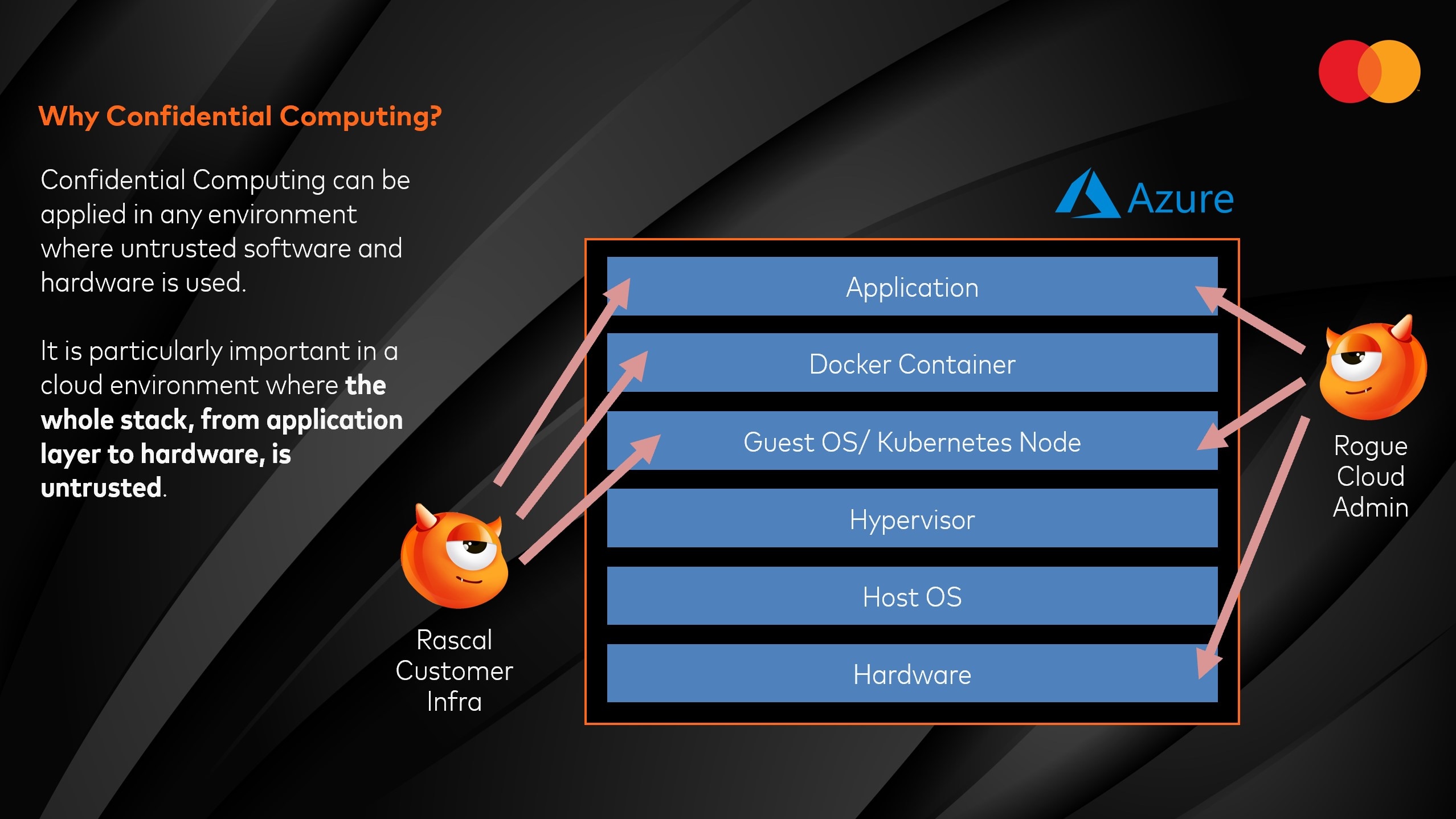
4. Secure Your Off-Chain Components: Confidential smart contracts often rely on secure oracles or trusted execution environments (TEEs) for external data feeds. Audit these components rigorously, as a single weak link can undermine your entire privacy stack.
Unlocking New DeFi Use Cases with Encrypted Contracts
The real excitement? Confidentiality isn’t just about hiding balances or trades, it unlocks entirely new categories of decentralized applications. Imagine:
- Private Auctions and OTC Trading: Run sealed-bid auctions where no one can front-run or spy on bids until settlement.
- Confidential Lending Pools: Lend or borrow without revealing your positions to competitors or surveillance bots.
- Censorship-Resistant Governance: Enable private voting mechanisms that protect voter anonymity while guaranteeing integrity.
- Secure Randomness and Gaming: Build games of chance and prediction markets with tamper-proof, verifiable randomness that remains hidden until reveal time.
What’s Next?
The future is bright, and wide open, for developers who master encrypted smart contracts today. As more protocols adopt FHE-powered solutions, composability between privacy-enabled dApps will become the new standard, not the exception.
If you’re serious about leading the next wave of blockchain innovation, now is the moment to level up your skills in secure DeFi development. Explore Zama’s resources (watch their video guide) and experiment with confidential computing layers like Secret Network (see use cases here). The tools are here, the only limit is how boldly you build.






