
In the ever-evolving world of decentralized finance (DeFi), the need for robust privacy and security has never been more critical. As DeFi platforms grow in complexity and value, so do the threats posed by front-running and Maximal Extractable Value (MEV) attacks. These exploitative practices undermine trust, siphon user profits, and distort fair market operations. Confidential smart contracts are now emerging as a powerful solution to these challenges, offering a new paradigm for encrypted DeFi transactions and MEV protection on the blockchain.
Understanding Front-Running and MEV in DeFi
Front-running occurs when malicious actors – often validators or specialized bots – observe pending transactions in the public mempool and strategically insert their own trades before or after them. The goal? To profit at the expense of unsuspecting users by manipulating transaction order, price, or execution timing. MEV takes this exploitation further by extracting value through reordering, inserting, or censoring transactions within a block. According to Hacken, these practices include displacement (pushing out genuine trades), suppression (delaying execution), or insertion (sandwiching trades for profit).
The consequences are tangible: higher slippage for traders, unpredictable gas fees, and a loss of confidence in DeFi protocols. Regular users face increased costs and reduced efficiency while sophisticated actors reap unfair rewards.
How Confidential Smart Contracts Disrupt Exploitation
The heart of MEV exploitation lies in transaction transparency. When every detail is visible on-chain before execution, adversaries can anticipate market moves and act accordingly. Confidential smart contracts flip this script by employing advanced encryption to conceal transaction data until finalization.
Key Cryptographic Techniques in Confidential Smart Contracts
-
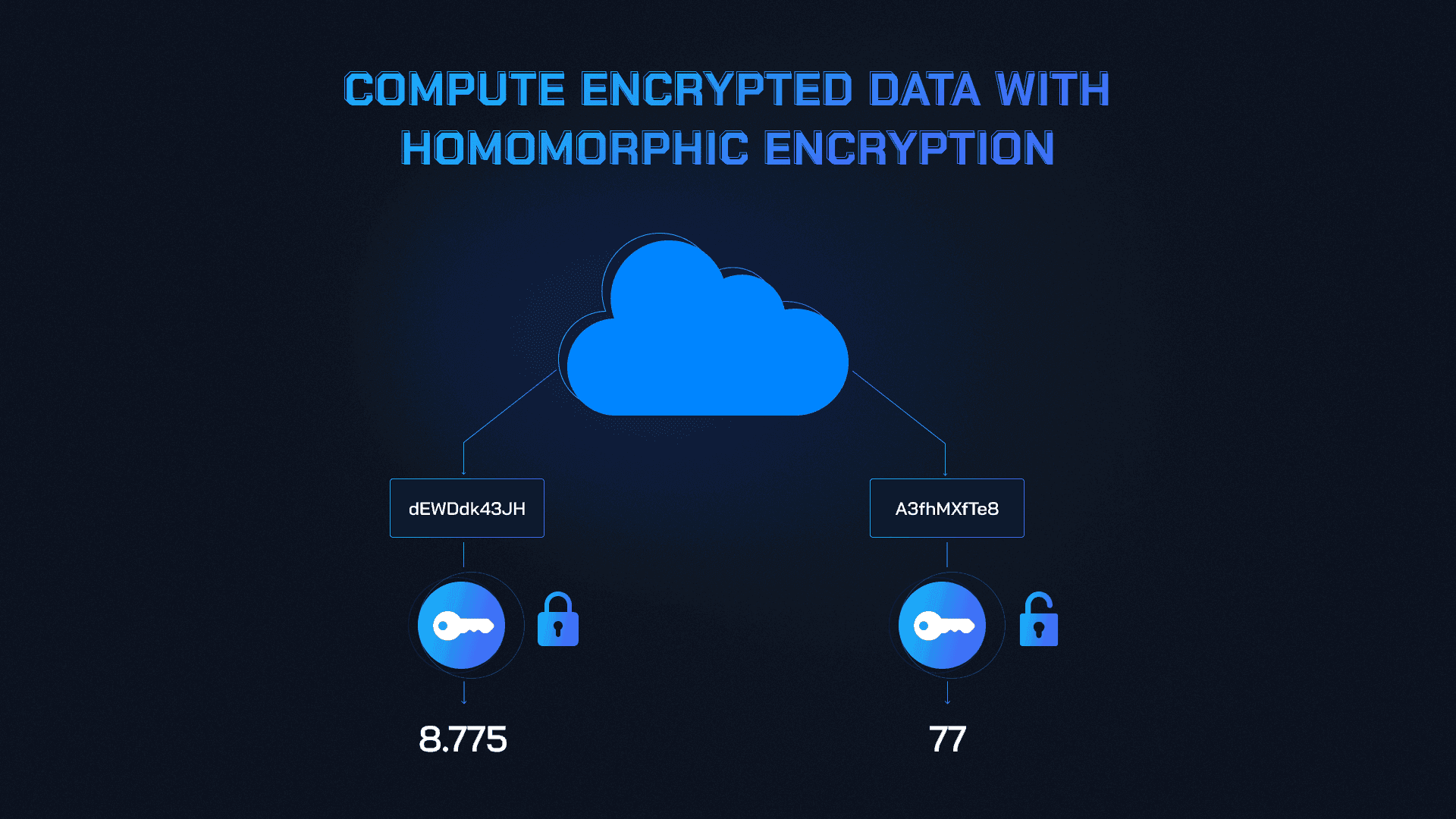
Fully Homomorphic Encryption (FHE): FHE enables computations on encrypted data without revealing underlying information. Projects like Fhenix leverage FHE to process DeFi transactions securely, ensuring transaction details remain confidential and immune to front-running.
-

Private, Anonymous, Collateralizable Commitments (PACCs): PACCs allow users to prove certain transaction attributes without exposing full details. This privacy-preserving commitment framework, as explored in Ethereum-based implementations, shifts MEV risk to censorship and prevents data leakage to potential attackers.
-

Threshold Cryptography: This technique encrypts transaction data and only decrypts it after consensus is reached. The F3B blockchain architecture uses threshold cryptography to maintain transaction privacy and protect against front-running throughout the consensus process.
Let’s break down some of the leading privacy-preserving technologies:
- Fully Homomorphic Encryption (FHE): FHE enables computations directly on encrypted data without requiring decryption first. This means that even contract logic can operate privately, no one sees your trade details until after execution is complete. Projects like Fhenix have integrated FHE to secure everything from financial swaps to in-game assets (fhenix.io), rendering real-time manipulation virtually impossible.
- Private Commitments and Threshold Cryptography: By encrypting user commitments until consensus is reached (as seen in threshold cryptographic schemes), confidential contracts prevent both validators and bots from accessing actionable information before it’s too late to exploit it (arxiv.org). This approach bolsters privacy throughout the process.
- PACCs Framework: Private, Anonymous, Collateralizable Commitments allow users to prove transaction attributes without revealing sensitive details, effectively shifting MEV risk away from transaction ordering toward censorship resistance (arxiv.org).
Real-World Impact: Fairness, Privacy, and Security for All
The adoption of confidential smart contracts brings transformative benefits to both individual traders and large-scale DeFi protocols:
- Prevention of Front-Running and MEV: Transaction data remains hidden until confirmed, shutting out would-be attackers who rely on advance knowledge.
- Transactional Fairness: Block proposers can no longer prioritize their own interests; all transactions are treated equally based on protocol rules rather than personal gain.
- Censorship Resistance: With less opportunity for selective inclusion or exclusion of transactions, DeFi becomes more open and equitable for all participants.
This shift is not just theoretical, leading protocols are already integrating these tools into production environments to safeguard user funds and bolster trust across the ecosystem.
While the technology is still evolving, the practical effects of confidential smart contracts are already visible in today’s DeFi landscape. By removing the information asymmetry that front-runners and MEV bots exploit, encrypted DeFi transactions restore a level playing field for all participants. This is particularly crucial as more institutional players and privacy-conscious users enter the market, demanding robust solutions that go beyond surface-level obfuscation.
Case studies from recent protocol launches demonstrate measurable improvements in user outcomes when confidential smart contracts are deployed. For example, platforms leveraging FHE or threshold cryptography have reported a dramatic reduction in sandwich attacks and slippage events during high-volume trading periods. These advances not only protect traders but also encourage higher liquidity, as users feel safer engaging with protocols that prioritize privacy and fairness.
Challenges and Considerations
Despite their promise, confidential smart contracts introduce new complexities for both developers and end-users. Performance overheads remain a concern, cryptographic operations like FHE can be resource-intensive, potentially increasing latency or gas costs on certain blockchains. Additionally, integrating privacy layers must be balanced with auditability and regulatory compliance; fully encrypted transactions can complicate forensic analysis or dispute resolution if not designed thoughtfully.
- Developer Tooling: Mature SDKs and libraries for building privacy-preserving contracts are still emerging, requiring ongoing investment from the open-source community.
- User Experience: Seamless wallet integrations and clear UX patterns are essential to ensure mainstream adoption doesn’t suffer due to added complexity.
- Protocol Interoperability: Ensuring confidential contracts can interact with existing DeFi infrastructure without breaking composability remains an active area of research.
The next wave of innovation will likely focus on optimizing these trade-offs, making privacy practical without sacrificing speed or usability. Projects like Fhenix (fhenix.io) are pioneering this space, offering modular solutions that plug into current DeFi workflows while delivering strong MEV protection on the blockchain.
Top Projects Advancing Confidential Smart Contracts in DeFi
-

Fhenix: Leveraging Fully Homomorphic Encryption (FHE), Fhenix enables smart contracts to process encrypted transactions, ensuring data confidentiality and robust protection against front-running and MEV attacks.
-
Secret Network: As the first blockchain with privacy-preserving smart contracts, Secret Network uses Trusted Execution Environments (TEEs) to keep transaction data private, effectively shielding users from MEV exploitation.
-

Aztec Protocol: Built on Ethereum, Aztec utilizes zero-knowledge proofs to enable confidential transactions and shielded DeFi operations, reducing the risk of transaction manipulation and front-running.
-
Oasis Network: Oasis combines confidential compute with blockchain technology, allowing smart contracts to process private data securely and prevent transaction data leakage that could lead to MEV.
-

Findora: Findora integrates zero-knowledge proofs and confidential assets to enable private DeFi transactions, thwarting front-runners and MEV bots from exploiting user data.
The Road Ahead: Privacy as a Core Pillar of DeFi Security
The momentum behind confidential smart contracts signals a broader shift in how the industry thinks about security. No longer is privacy an afterthought, it’s foundational to building resilient protocols capable of withstanding sophisticated adversaries. As regulatory frameworks evolve and user expectations rise, encrypted contract solutions will become table stakes for any serious DeFi platform seeking long-term relevance.
If you’re building or investing in decentralized finance today, prioritizing MEV-resistant architecture isn’t just prudent, it’s essential for sustainable growth. The era of open mempool surveillance is ending; in its place arises a new standard where every participant can transact freely without fear of exploitation.
Empowering privacy, one contract at a time, confidential smart contracts aren’t just preventing front-running; they’re redefining what it means to trust code over intermediaries in the digital economy.






