Encrypted voting systems are rapidly moving from academic theory to practical deployment, driven by the need for secure, transparent, and private elections. Traditional electronic voting methods have long struggled with issues like identity theft, ballot manipulation, and lack of verifiability. Blockchain technology, when combined with advanced cryptography, offers a promising solution. By leveraging privacy smart contracts, developers can create voting systems that ensure every ballot remains confidential while the process itself is auditable and tamper-resistant.
Why Privacy Matters in Blockchain Voting
The promise of blockchain-based voting is decentralization and transparency. However, without proper privacy safeguards, voter anonymity can be compromised. Public blockchains are inherently transparent; every transaction is visible to all participants. This creates a paradox for elections: we want ballots to be recorded immutably on-chain but without exposing how individuals voted.
Recent research highlights that existing e-voting platforms often fail due to insufficient privacy controls or centralized vulnerabilities (ScienceDirect.com). To address these issues, privacy smart contracts integrate cryptographic primitives such as homomorphic encryption and zero-knowledge proofs. These tools allow for vote tallying and eligibility verification without revealing sensitive data.
Core Technologies Behind Encrypted Voting Systems
To build robust encrypted voting systems using privacy smart contracts, several key technologies must work together:
Key Cryptographic Techniques in Blockchain Voting
-
Homomorphic Encryption: Enables encrypted votes to be tallied without decryption, preserving voter privacy while ensuring accurate results. Widely used in blockchain voting prototypes for secure aggregation.
-
Zero-Knowledge Proofs (ZKPs): Allow voters to prove their eligibility and the correctness of their vote without revealing any personal or ballot information. ZKPs are integral to privacy-preserving voting systems on blockchains like Ethereum.
-

Secure Multi-Party Computation (MPC): Multiple parties collaboratively compute election results without exposing individual votes, ensuring that no single entity can access all voting data. MPC enhances trust in decentralized voting platforms.
-
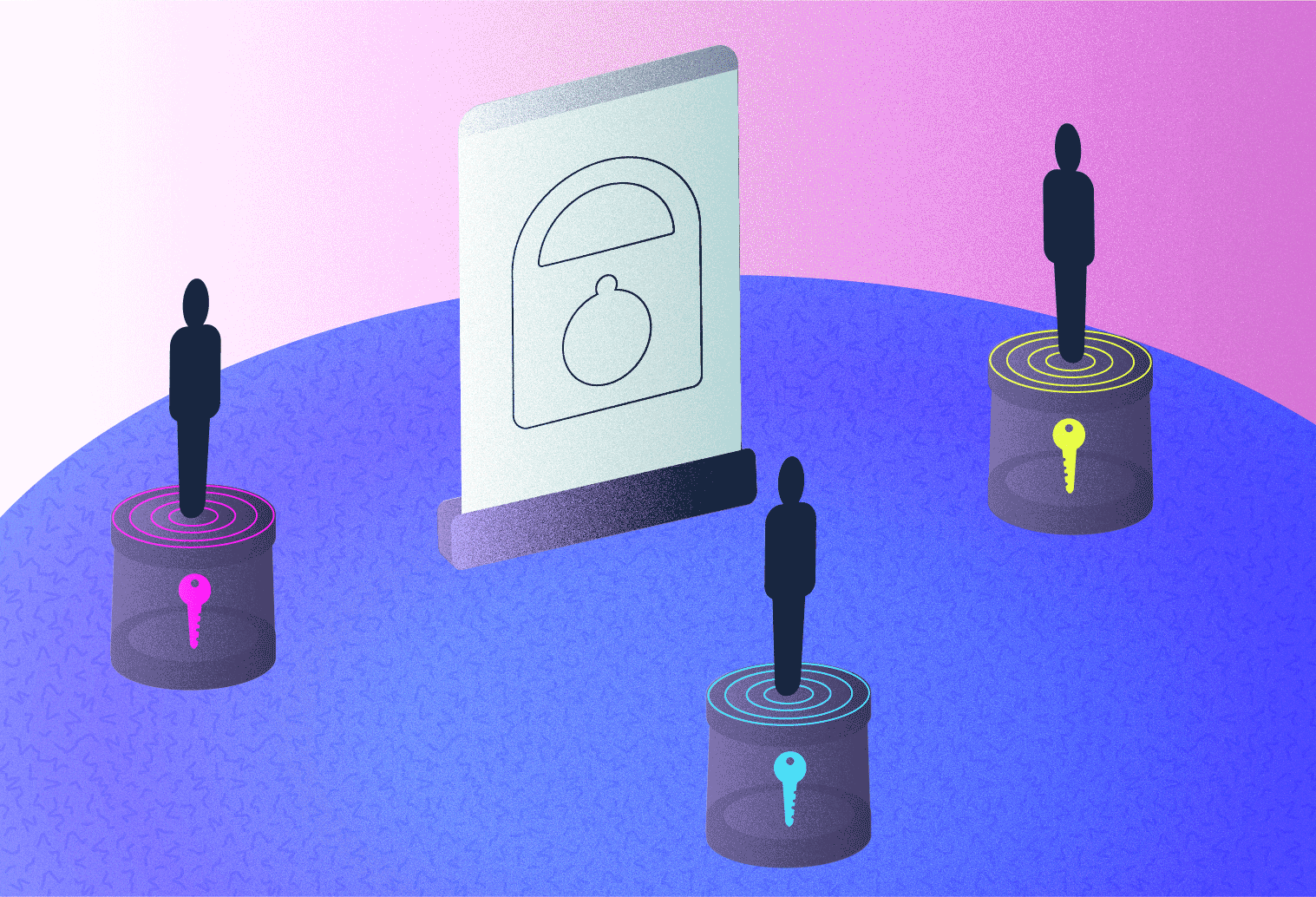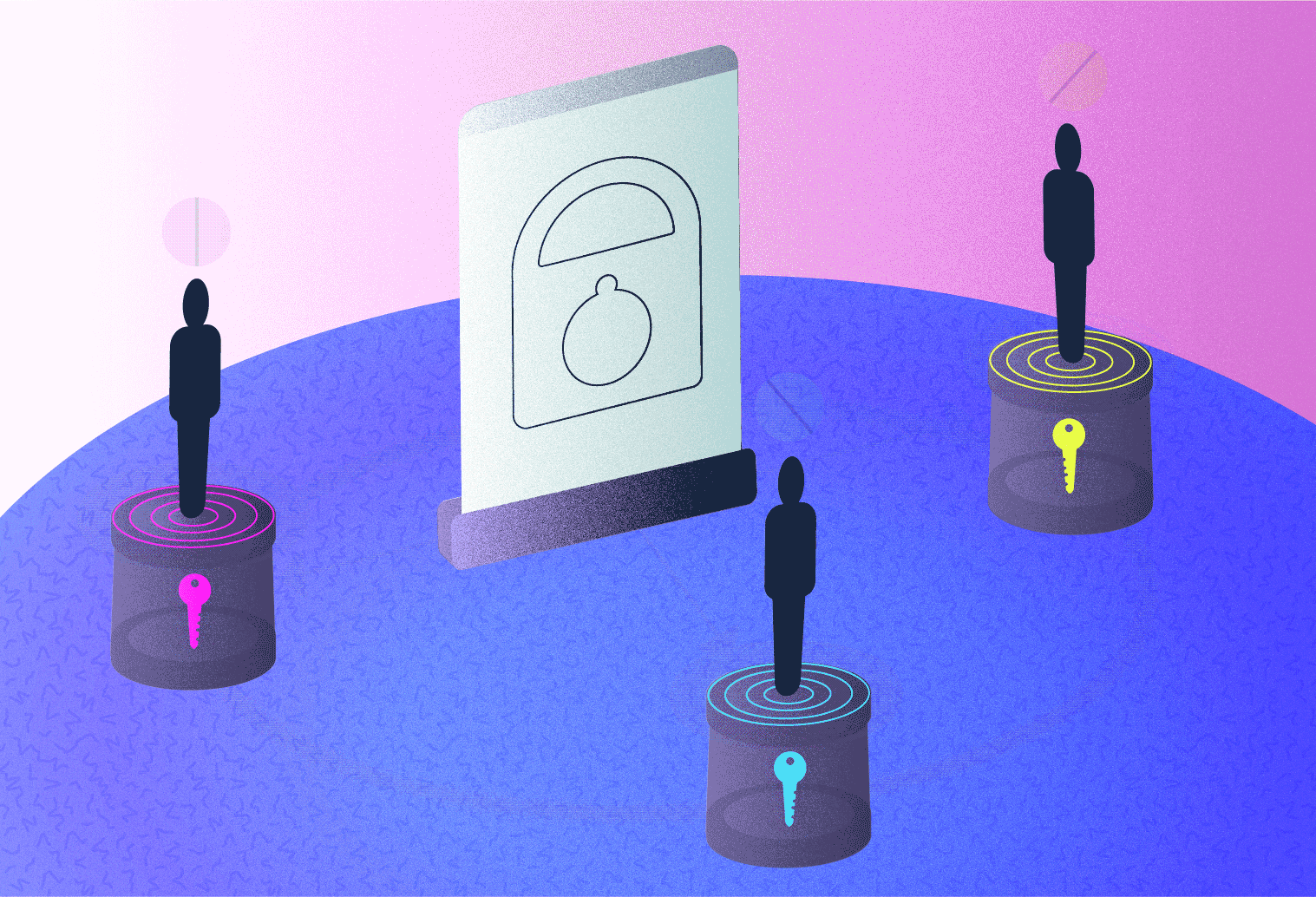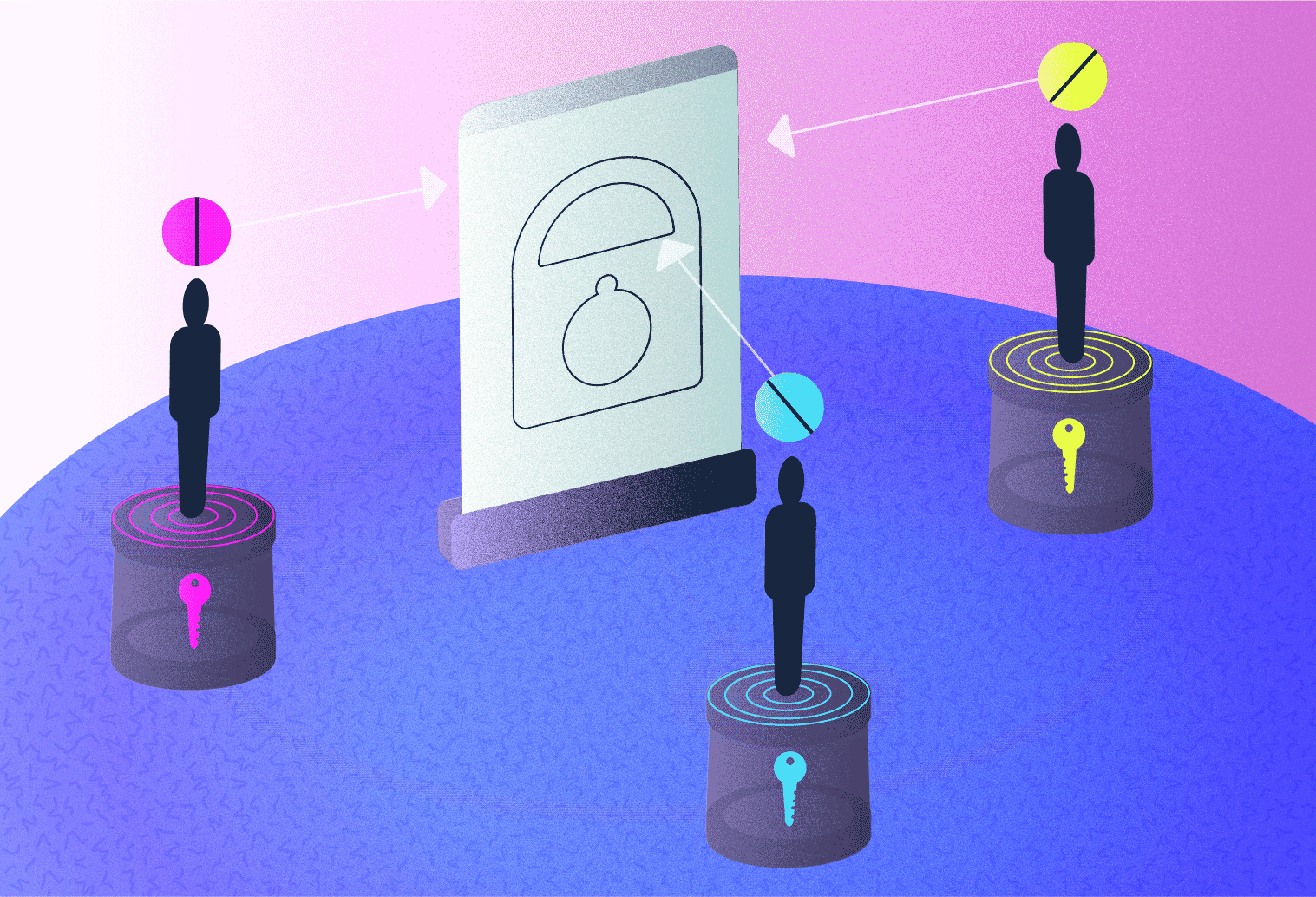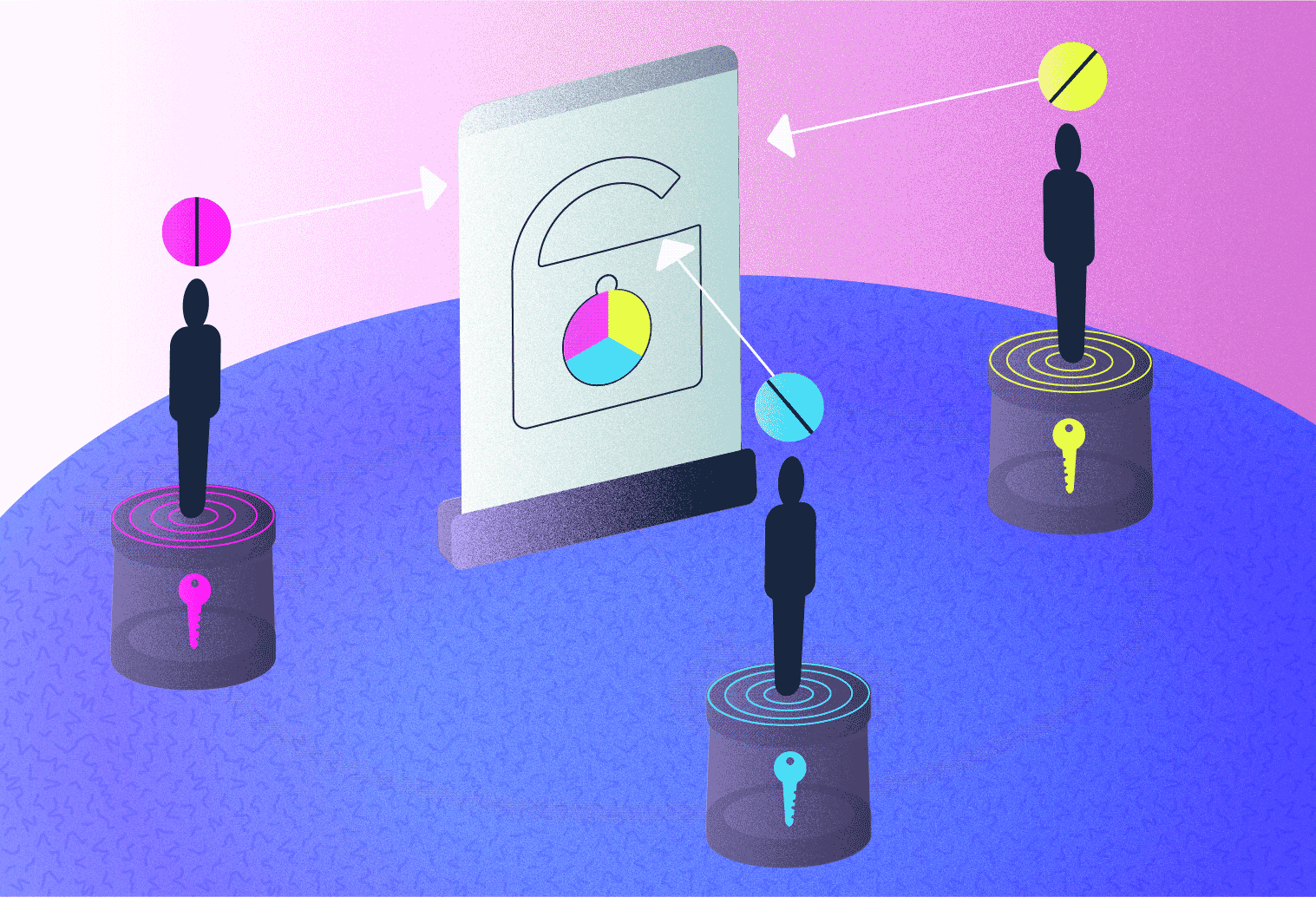
Threshold Encryption: Requires a minimum number of trusted parties to decrypt election results, preventing any single party from accessing sensitive data. This technique is crucial for distributed trust in blockchain-based elections.
-

End-to-End Verifiability: Systems such as Scantegrity let voters confirm their votes are counted correctly, building trust and transparency in digital elections.
Homomorphic Encryption: This enables mathematical operations on encrypted data. In practice, it allows vote tallies to be computed without decrypting individual ballots (digitaldemocracyforum.com). Voters’ choices remain secret throughout the process.
Zero-Knowledge Proofs (ZKPs): ZKPs allow voters to prove their eligibility, and that their vote was correctly formed, without revealing their identity or vote content (ijert.org). This prevents double voting and ensures only legitimate ballots are counted.
Secure Multi-Party Computation (MPC): With MPC, multiple entities jointly perform computations (like tallying votes) over encrypted inputs so that no single party ever sees the full dataset (en.wikipedia.org). This decentralizes trust and mitigates risks of insider attacks.
Threshold Encryption: Decryption keys are split among several trusted parties; only a quorum can decrypt the final tally (blog.shutter.network). This protects against collusion or coercion by any single actor.
The Role of Privacy Smart Contracts in Secure Elections
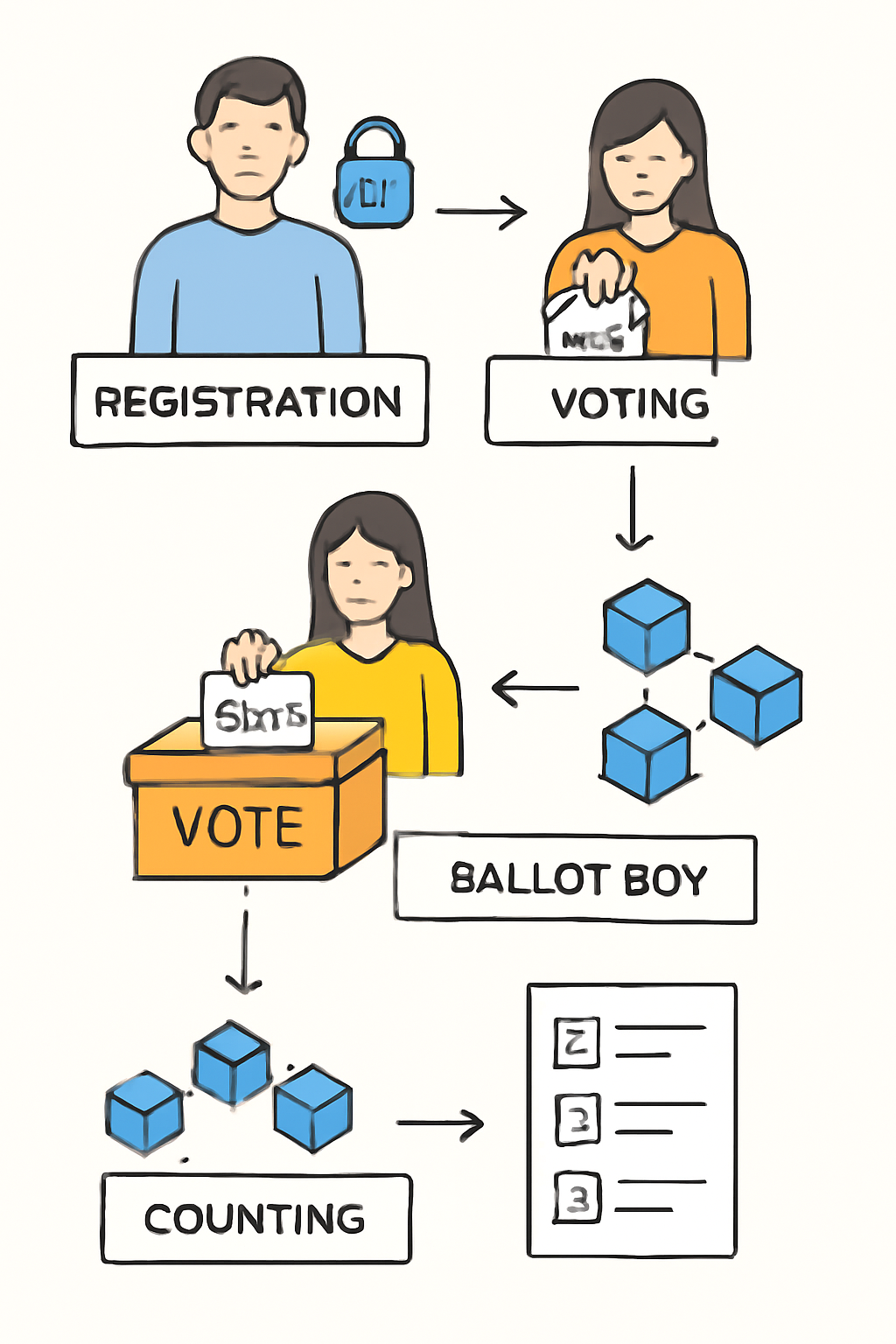
Privacy smart contracts act as autonomous arbiters on-chain. They enforce rules for voter registration, ballot casting, and tallying, without ever exposing raw votes or personal data. Platforms like Ethereum and Tezos have been used for such deployments (electis.com). Smart contracts written with privacy features ensure:
- Anonymity: Voter identities remain unlinkable to their ballots.
- Immutability: Once cast, votes cannot be altered or deleted.
- End-to-End Verifiability: Every participant can audit that all valid votes were counted correctly without exposing individual choices.
- No Single Point of Failure: Decentralized execution removes reliance on a central authority vulnerable to compromise or censorship.
The intersection of these technologies makes it possible to design elections where voters trust both the secrecy of their ballot and the legitimacy of the outcome, a crucial step forward in digital democracy.
Still, practical deployment of encrypted voting systems comes with unique challenges. Scalability is a persistent hurdle: advanced cryptographic computations, especially homomorphic encryption and zero-knowledge proofs, can be resource-intensive. Developers must strike a balance between privacy guarantees and network performance. Recent frameworks like EtherVote and SmartphoneDemocracy demonstrate that with careful system design and optimization, encrypted voting is feasible even at national scales.
User experience is another critical concern. Voters should not need to understand the underlying cryptography to participate securely. Intuitive interfaces, clear instructions, and robust voter authentication, often leveraging decentralized identity solutions, are essential for widespread adoption. Security audits and formal verification of smart contracts further bolster trust in these systems.
Best Practices for Implementation
To ensure both security and usability in blockchain voting projects, teams should adopt several best practices:
Best Practices for Deploying Encrypted Voting Systems
-

Conduct Rigorous Usability Testing: Ensure the voting interface is intuitive and accessible for all eligible voters. Platforms like Electis demonstrate the importance of user-friendly design and comprehensive testing to minimize voter errors and maximize participation.
-
Implement Formal Verification of Smart Contracts: Use formal methods to mathematically prove the correctness and security of smart contracts. Tezos is recognized for supporting formal verification, helping prevent vulnerabilities and ensuring contract reliability.
-

Adopt Multi-Party Key Management: Enhance security by distributing cryptographic keys among multiple trusted parties. Secure Multi-Party Computation (MPC) and Threshold Encryption are widely used to prevent any single entity from compromising vote secrecy.
-
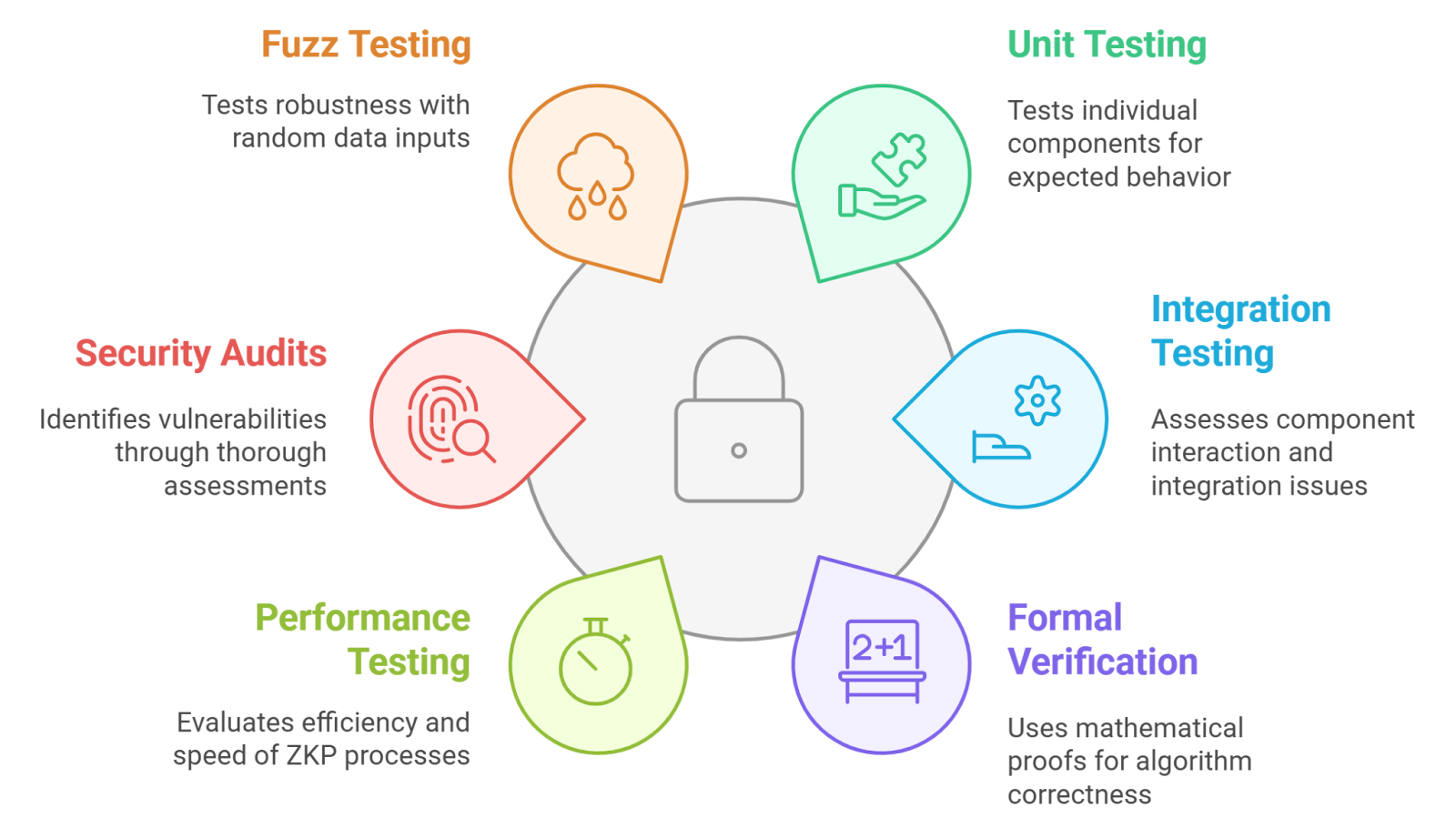
Integrate Zero-Knowledge Proofs for Privacy: Utilize zero-knowledge proofs to verify voter eligibility and vote integrity without revealing sensitive data. Solutions leveraging zero-knowledge cryptography are gaining traction in privacy-preserving e-voting systems.
-
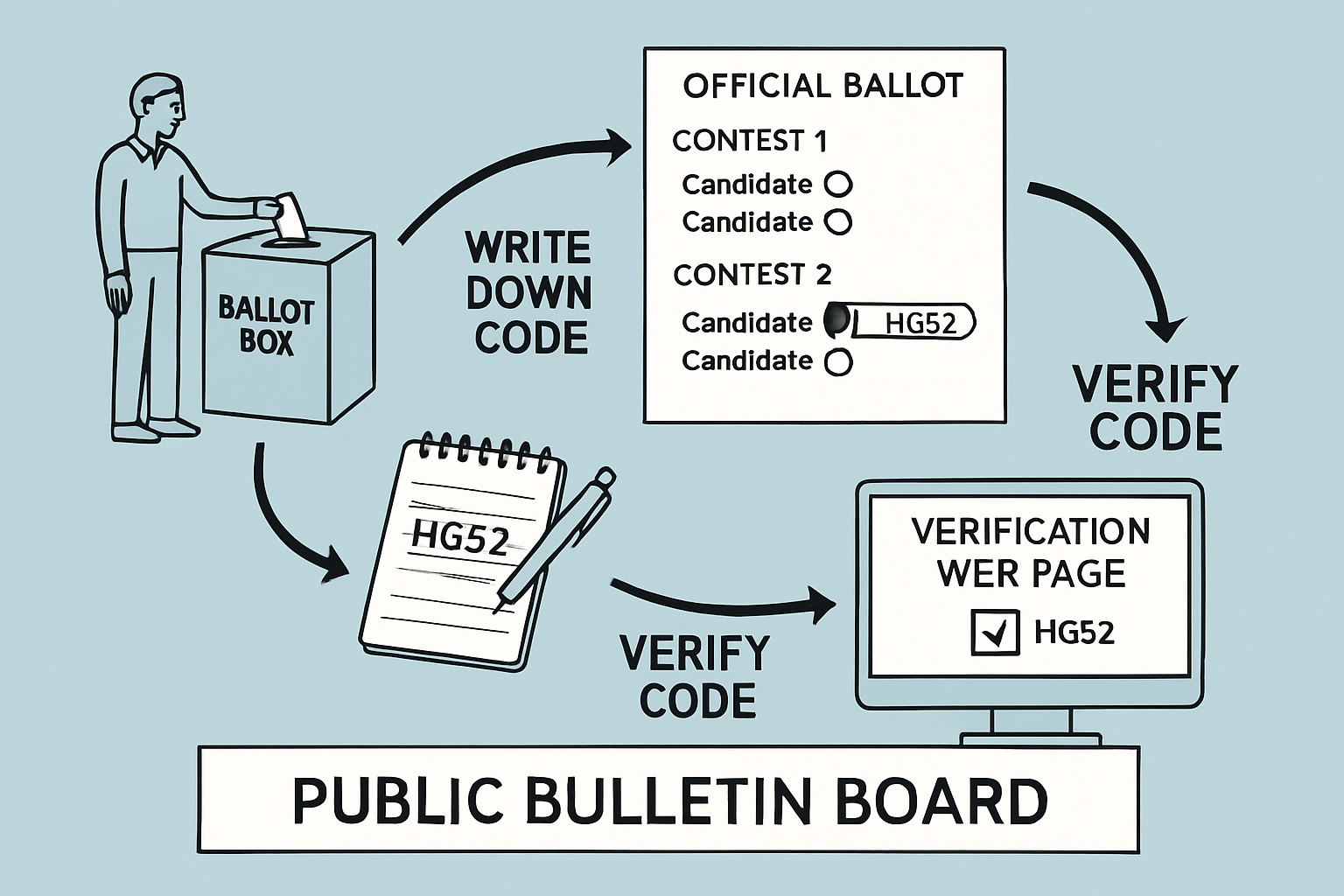
Ensure End-to-End Verifiability: Deploy systems such as Scantegrity to allow voters to independently verify that their votes are recorded and counted as intended, building public trust in the election process.
Start by integrating strong voter authentication mechanisms to prevent unauthorized access. Use threshold encryption or MPC to distribute trust among multiple parties, no single entity should control the decryption keys or vote tallying process. And always provide end-to-end verifiability so voters can confirm their ballot was counted without revealing its content.
Testing under real-world conditions is vital. Simulate attacks such as Sybil attacks or denial-of-service attempts; continuously monitor for vulnerabilities in both the smart contracts and the user-facing application layer. Transparency reports and open-source code reviews build confidence among stakeholders and the broader public.
Emerging Trends: Towards Scalable, Universal Adoption
The landscape of encrypted voting systems continues to evolve rapidly. New advances in succinct zero-knowledge proofs (like zk-SNARKs) are making privacy-preserving computations faster and more scalable. Integration with national digital ID wallets, such as those piloted in SmartphoneDemocracy, promises seamless onboarding while maintaining privacy (arXiv). Meanwhile, initiatives like Scantegrity push end-to-end verifiability further by allowing voters to independently audit their participation (en.wikipedia.org).
The future likely holds more hybrid models that combine on-chain privacy contracts with off-chain computation layers or trusted hardware enclaves for even greater efficiency without sacrificing security.
Encrypted voting systems built on privacy smart contracts are not just a technological upgrade, they represent a fundamental shift towards more transparent, trustworthy, and resilient democratic processes.