As privacy-preserving smart contracts gain traction across decentralized finance and enterprise blockchain, the stakes for secure key management have never been higher. The cryptographic keys that underpin these contracts are the linchpin of both privacy and trust. A single misstep in their handling can unravel even the most sophisticated encrypted contract security, exposing sensitive data and undermining user confidence. In this rapidly evolving landscape, best practices are not optional, they are mission critical.
The Strategic Role of HSMs and TEEs in Key Generation and Storage
Generating and storing cryptographic keys within Hardware Security Modules (HSMs) or Trusted Execution Environments (TEEs) is non-negotiable for any serious privacy smart contract deployment. HSMs provide tamper-resistant hardware designed specifically for secure key operations, while TEEs like Intel SGX or ARM TrustZone create isolated environments that protect sensitive computations from the rest of the system. These technologies ensure that private keys never leave protected memory, drastically reducing exposure to malware or insider threats.
This approach is endorsed by industry research, which emphasizes that generating keys inside trusted modules rather than in software environments is a foundational pillar for encrypted contract security (source). When integrated with smart contracts, these modules act as a robust first line of defense against both external attackers and internal compromise.
Implementing Robust Key Rotation and Revocation Policies
No cryptographic key should be considered eternal. Key rotation, the process of periodically replacing old keys with new ones, is vital to limit the window of opportunity for attackers. Similarly, key revocation policies allow organizations to quickly invalidate compromised or outdated keys, an essential control in the event of a breach or personnel change.
The operational challenge lies in designing automated systems that can rotate and revoke all contract-related keys without disrupting ongoing transactions or breaking privacy guarantees. Smart contract platforms that support seamless asset migration between rotated keys are preferable, as they minimize downtime while maximizing security posture (source). This discipline is especially important given regulatory scrutiny around data protection in decentralized systems (source).
Access Controls and Audit Trails: Zero Tolerance for Unauthorized Usage
Strict access controls, combined with comprehensive audit trails, form the backbone of operational security in decentralized environments. Every interaction with a private key should be governed by granular permissions, ideally leveraging role-based access control (RBAC) frameworks, and logged immutably for forensic analysis.
This approach not only deters insider threats but also provides an evidentiary record if suspicious activity arises. In permissioned blockchains or enterprise settings, integrating these controls with existing identity management solutions can further streamline compliance efforts and bolster overall governance.
Top 5 Secure Key Management Practices for Privacy-Preserving Smart Contracts
-

Utilize Hardware Security Modules (HSMs) or Trusted Execution Environments (TEEs) for Key Generation and Storage: Deploy HSMs (e.g., AWS CloudHSM, IBM Cloud HSM) or TEEs (such as Intel SGX, ARM TrustZone) to securely generate, store, and manage cryptographic keys, ensuring isolation from potentially compromised systems.
-
Implement Robust Key Rotation and Revocation Policies for All Contract-Related Keys: Establish automated procedures for regular key rotation and immediate revocation in response to threats. Use platforms like HashiCorp Vault to manage lifecycle events and enforce policy compliance.
-
Enforce Strict Access Controls and Audit Trails for Key Usage in Decentralized Environments: Apply role-based access control (RBAC) and maintain comprehensive audit logs with solutions like AWS Key Management Service (KMS) or Azure Key Vault to monitor and restrict who can access and use keys.
-

Adopt Secure Multi-Party Computation (MPC) or Threshold Cryptography to Distribute Key Control: Leverage MPC platforms such as Fireblocks MPC Wallet or Curv to split key control among multiple parties, eliminating single points of failure and enhancing contract security.
-

Ensure Off-Chain Secure Backup and Recovery Procedures for Critical Keys: Create encrypted, geographically distributed backups using established solutions like Trezor hardware wallets, Ledger, or Shamir Backup, and regularly test recovery processes to guarantee business continuity.
The sophistication required here cannot be overstated: as attacks targeting privileged credentials become more advanced, real-time monitoring and anomaly detection around key usage are fast becoming industry standards rather than aspirational goals.
Yet, even the most advanced access controls are only as strong as their weakest link. That’s why organizations must continuously test and refine their permissioning models, ensuring that only authorized parties can access or operate on cryptographic keys. Regular audits, both internal and external, help identify gaps before they are exploited. The ability to produce a clear, tamper-proof audit trail is not just a security imperative but also a regulatory necessity for businesses operating in privacy-sensitive sectors.
Distributed Key Control: Multi-Party Computation and Threshold Cryptography
Centralized key custody is fundamentally incompatible with the ethos of decentralized finance and privacy smart contracts. Enter Secure Multi-Party Computation (MPC) and threshold cryptography: these cryptographic techniques split control of a private key among several independent parties or devices. No single entity ever holds the complete key, eliminating single points of failure and dramatically reducing the risk from both external hackers and malicious insiders.
MPC protocols require multiple parties to collaborate, often in real time, to authorize any sensitive operation involving keys. This not only raises the bar for attackers but also enables flexible governance models such as multi-signature approvals or geographically distributed trust anchors. For high-value contracts or those managing sensitive off-chain data, adopting MPC is quickly becoming a best practice rather than an experimental feature (source).
Threshold cryptography further enhances resilience by requiring only a subset (threshold) of participants to reconstruct a key or sign a transaction. This provides operational flexibility while maintaining robust security guarantees, if one share is lost or compromised, adversaries still cannot access the full key.
Off-Chain Secure Backup and Recovery: Planning for the Inevitable
No matter how sophisticated your on-chain protections are, disaster recovery remains an essential pillar of encrypted contract security. Off-chain secure backup and recovery procedures ensure that critical keys can be restored in case of accidental loss, catastrophic system failure, or targeted attack.
The gold standard here involves encrypted backups stored in multiple physically secure locations, think geographically dispersed data centers with restricted access controls. Backups should themselves be protected by strong encryption and subject to periodic integrity checks. Organizations must also develop clear playbooks for recovery processes: who can initiate them, what steps are required for verification, and how to minimize downtime without sacrificing confidentiality.
This approach aligns with recommendations from industry experts who stress that backup strategies must be both technically sound and operationally practical (source). In regulated environments or when managing significant assets on behalf of users, formalizing these procedures isn’t just prudent, it’s essential for long-term resilience.
Strategic Takeaways for Privacy Smart Contract Developers
The landscape of secure key management is evolving rapidly alongside advances in privacy-preserving smart contracts. By focusing on these five critical practices, leveraging HSMs/TEEs, enforcing rotation/revocation policies, instituting rigorous access controls with audit trails, distributing control via MPC/threshold schemes, and ensuring robust off-chain backup, organizations can dramatically reduce their attack surface while maintaining compliance and user trust.
The future belongs to those who treat encrypted contract security not as a checklist item but as an ongoing discipline, a blend of technology, policy, and vigilance that adapts to new threats without sacrificing usability or innovation.
Top 5 Best Practices for Secure Key Management
-

Utilize Hardware Security Modules (HSMs) or Trusted Execution Environments (TEEs) for Key Generation and Storage: Deploying HSMs such as AWS CloudHSM or TEEs like Intel SGX ensures that cryptographic keys are generated and stored in isolated, tamper-resistant environments, significantly reducing exposure to attacks.
-
Implement Robust Key Rotation and Revocation Policies for All Contract-Related Keys: Regularly update and rotate cryptographic keys, and promptly revoke compromised or obsolete keys. This minimizes the risk window for attackers and supports compliance with evolving security standards.
-
Enforce Strict Access Controls and Audit Trails for Key Usage in Decentralized Environments: Apply granular access permissions using established identity and access management tools, and maintain immutable audit logs—such as those provided by AWS CloudTrail—to monitor and trace all key-related activities.
-
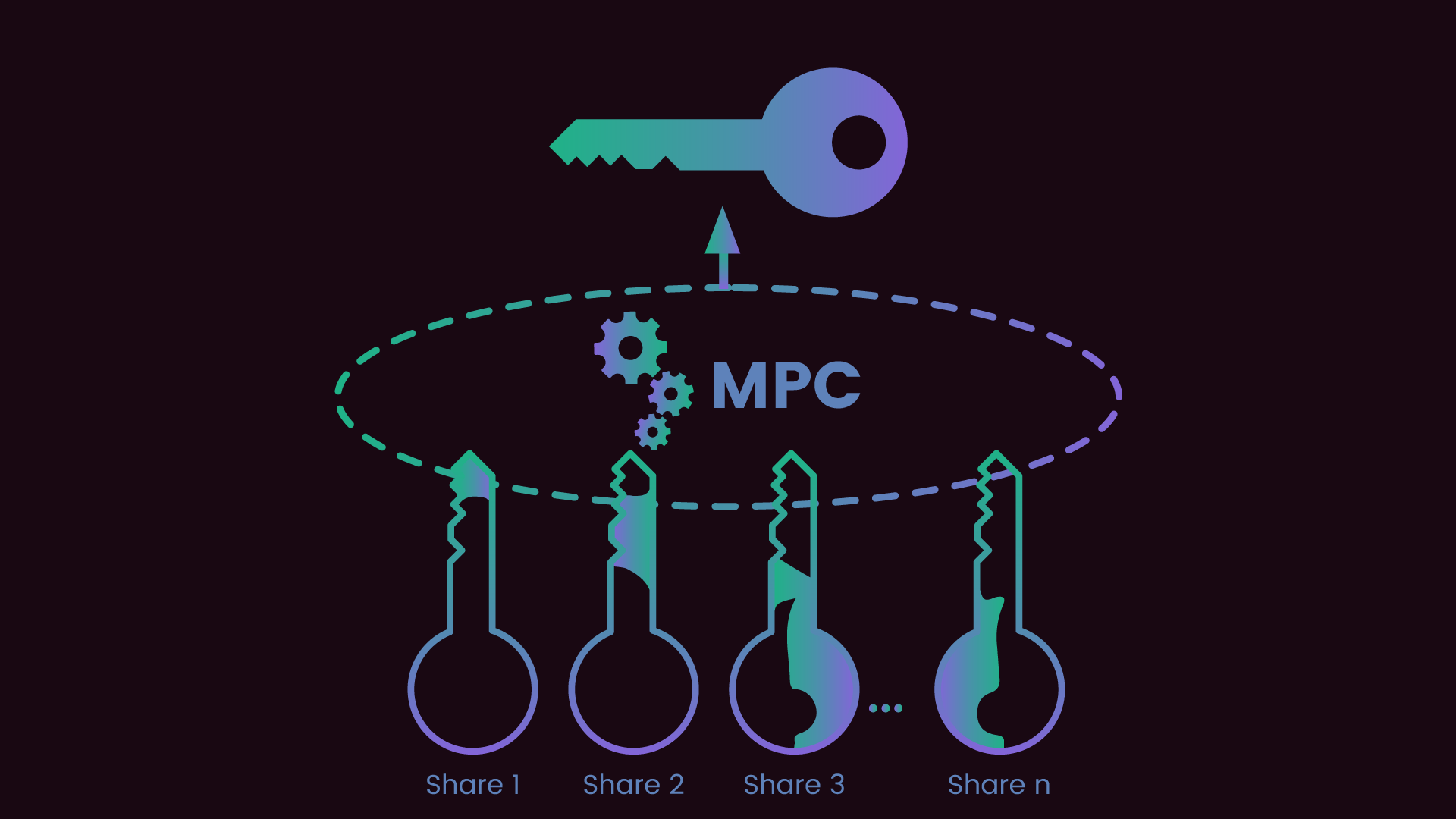
Adopt Secure Multi-Party Computation (MPC) or Threshold Cryptography to Distribute Key Control: Leverage solutions like Fireblocks MPC Wallet to split key material among multiple parties, eliminating single points of failure and requiring consensus for sensitive operations.
-

Ensure Off-Chain Secure Backup and Recovery Procedures for Critical Keys: Store encrypted backups in geographically diverse, physically secure locations using trusted services such as HashiCorp Vault, and regularly test recovery processes to guarantee business continuity.